In a nutshell: British researchers have developed an AI capable of identifying keystrokes through their acoustic signatures. Using a smartphone as a microphone positioned near a laptop, they trained the AI by correlating the unique sound of each keystroke with its corresponding letter. When a password was typed into the laptop, the AI successfully deciphered the word from the keystroke sounds with a remarkable 95 percent accuracy.
Imagine typing away on your laptop, logging into an account or two, while your phone silently sits beside you. Here's the scary part: it could be eavesdropping on every click and clack, feeding data to an AI that's learning your most private information. While this might sound like a plot from a sci-fi thriller, it's closer to reality than we might think, highlighting the fine line between the benefits of AI and its not-so-stellar quirks.
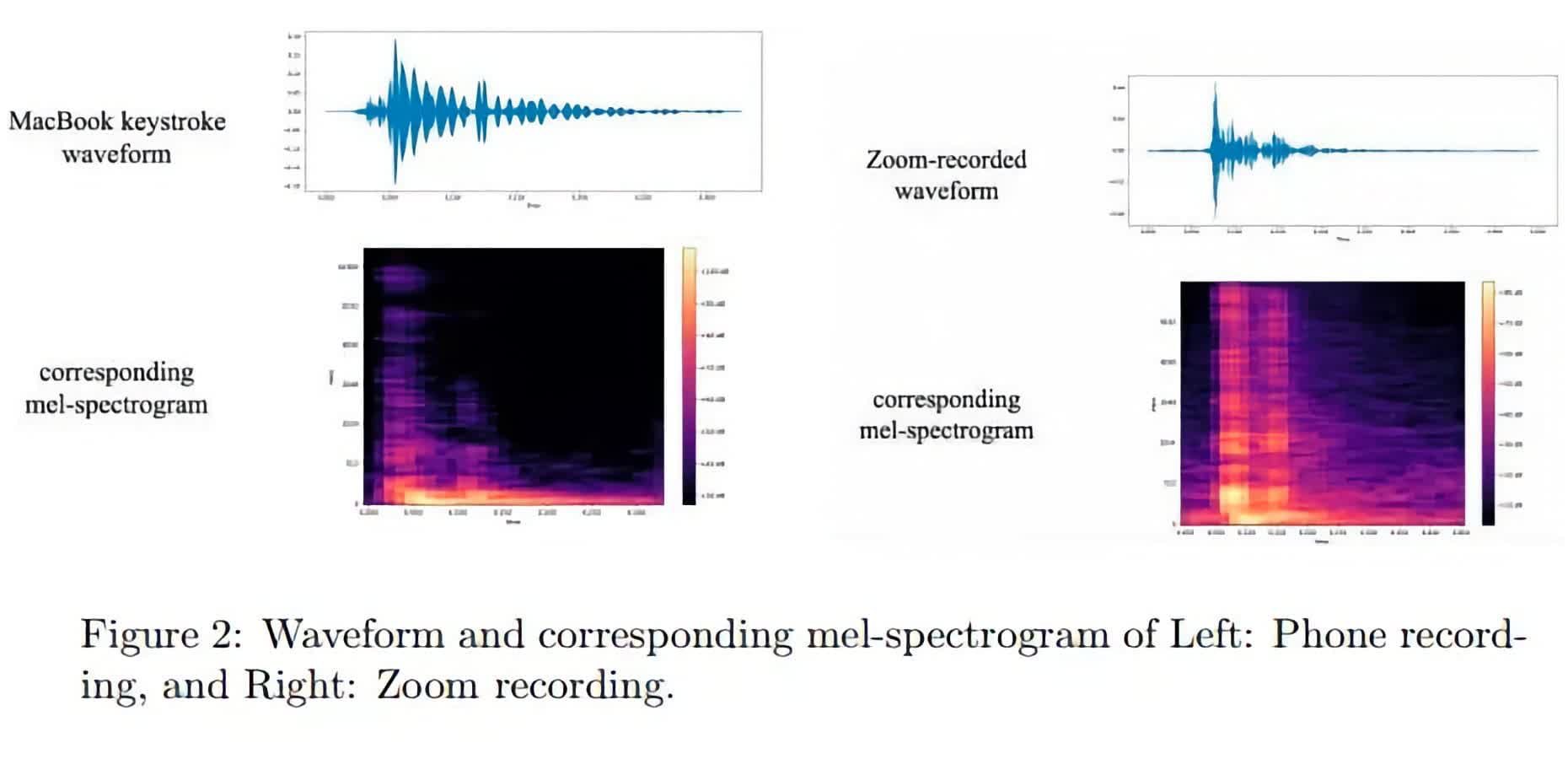
Armed with deep-learning algorithms, the research team developed a system to identify what you're typing based solely on the sound of your keyboard. Named CoAtNet, the AI was trained using spectrograms representing the unique sound each key produces. The result is a 95% success rate in deciphering keystrokes, using just a smartphone placed 20 centimeters away from a MacBook.
Dr. Ehsan Toreini, a co-author of the study, says that she expects "the accuracy of such models, and such attacks, to increase," as most modern smart devices are equipped with microphones. The team also tested their AI over Zoom and Skype calls, achieving nearly the same level of accuracy.
But before you start panicking and throwing out every tech device in your house, there are some obvious limitations in the current model. CoAtNet needs to be tailored to each keyboard type, as sounds between keyboards will vary. The training involved pressing each of the 36 keys on a MacBook – including letters and numbers – 25 times in a row using different fingers and varying pressure levels.
Also, the AI struggles with the nuances of the Shift key, so mixing up your password with upper and lower cases, numbers, and symbols is a good start.
The study primarily serves as a proof-of-concept and hasn't been utilized for actual password cracking or in real-world environments like coffee shops, where a noisier environment can make eavesdropping less practical or usable. The researchers however noted that laptops, with their uniform keyboards and frequent use in public spaces, are particularly susceptible to such techniques. Keyboard modders might find it interesting that altering a keyboard's acoustic properties will render the AI ineffective, requiring new training for the system.
But the best defense in this instance may be your good old password manager, as they can auto-fill passwords, making them immune to this acoustic espionage. Adding two-factor authentication and biometric options like fingerprint scans and facial recognition to the mix will make things more airtight.
Ultimately, the study means to raise awareness about the advanced abilities of AI algorithms in extracting insights from novel data types. Acoustic signals, often utilized in side-channel attacks like those involving laser microphones, are now subject to even more sophisticated analysis through advanced machine learning techniques.
