Kaspersky has published its findings on the massively distributed Flame malware it identified four months ago, revealing that evidence found on Command & Control (C&C) servers suggests the strain dates back as far as 2006. Researchers also learned that the servers support another three pieces of unidentified malware, one of which is circulating the Internet.
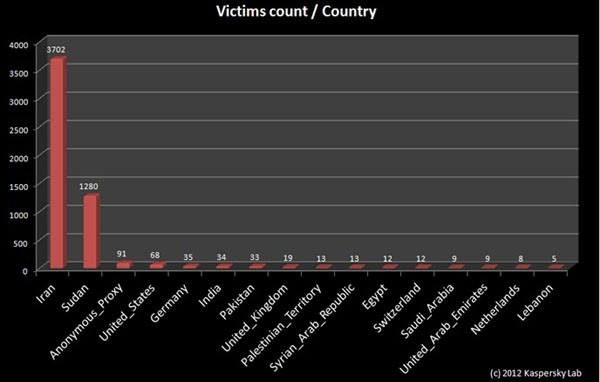
Forensic experts got a lucky break after the C&C operators made a couple of mistakes. In addition to accidently locking themselves out of one server containing data about their activities, they incorrectly configured their shred script on a second server by misspelling its filename. The first server had uploaded more than 5GB of data from over 5,000 infected computers (bottom image) in one week.
"That's pretty staggering," Vikram Thakur of Symantec Security Response said. "If the attackers actually continued their operations in a similar manner or with high frequency over the past five years they probably have terabytes of information collected from pretty much whoever they chose."
In conjunction with agencies including Symantec, Kaspersky's analysis has revealed that the C&C servers used four different communication protocols: OldProtocol, OldProtocolE, SignupProtocol and RedProtocol, which has not yet been implemented so very little is known about it. These handle communications for four separate clients: SP, SPE, IP and FL, which was later identified as Flame. Based on their HTTP requests, the remaining three clients are not Duqu, Gauss or Stuxnet.
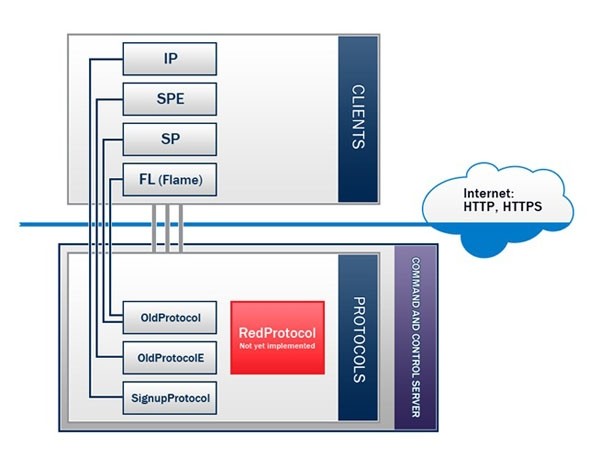
To learn more about the malware, Kaspersky set up a sinkhole server for Flame and found it communicated through the connection Oldprotocol. The unidentified IP and SP malware received no hits, while researchers learned that SPE via OldProtocolE is functioning in the wild.
Kaspersky didn't say how many C&C servers were involved, but it noted that the systems ran Debian Linux set up with an automated script, which could indicate that there were too many servers to manage manually. The script also installed chkconfig, a tool found on Red Hat-based distros that disables or enables system services. Debian has different utilities for this functionality, so Kaspersky believes the hackers opted for chkconfig out of comfort because they might have previously used the Red Hat-derived CentOS.
Interestingly, to the unsuspecting eye, the C&C server's site looked like CMS software and Kaspersky initially thought it was an early alpha version of a botnet C&C server. After gaining access, the security experts realized this was a deliberate attempt to hide the true function of the server from the hosting company. In that same vein, the hackers used control panel labels like "data," "upload" and "download" instead of "bot," "botnet," "infection" or "malware-command."
Kaspersky noted that the C&C server had a high level of security. The hackers encrypted every upload and they created many user accounts with varying levels of permission, including some that couldn't access the encrypted data. The data's decryption keys weren't kept on the server either, which suggests only certain members of the team could view them offline. According to Kaspersky, this is very unusual and further reinforces the firm's belief that this is a state-sponsored operation.
Additionally, the hackers configured scripts to regularly remove traces of activity, and there appears to have been mechanisms in place to prevent the server from exceeding its total storage capacity. Once the disk was full, it removed old entries to make room for the new ones.
The report concluded that development of the C&C code started as early as December 2006, and the handles of four programmers have so far been identified in comments saved to the servers. The most recent update was on May 18, 2012.
