Your browser or password manager's form autofill feature can be a big time saver, automatically entering data like your name, address, and phone number on those lengthy sign up or check out screens. But as Finnish web developer and hacker Viljami Kuosmanen points out, you might be inadvertently giving away more information than you are willing to share with a particular website.
The proof-of-concept phishing attack is incredibly simple. Essentially, when browsers like Chrome and Safari autofill information into text boxes, they don't really discriminate between visible and invisible form fields. A malicious website could be showing fields for name and email address, while hiding boxes for more sensitive data like phone number, address, and even credit card number.
The malicious website can be designed to look like a legitimate service you actually use, and trick people into entering seemingly innocuous information without them noticing what was actually being sent.
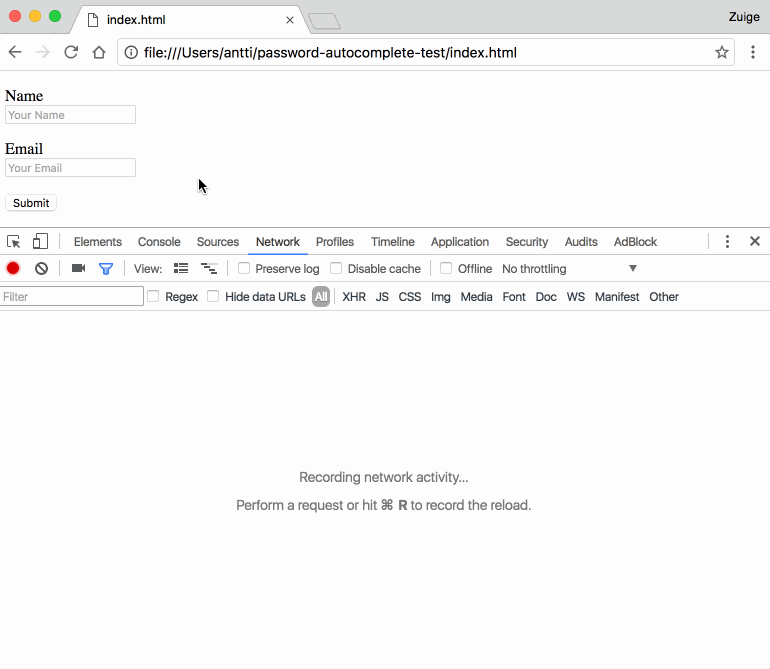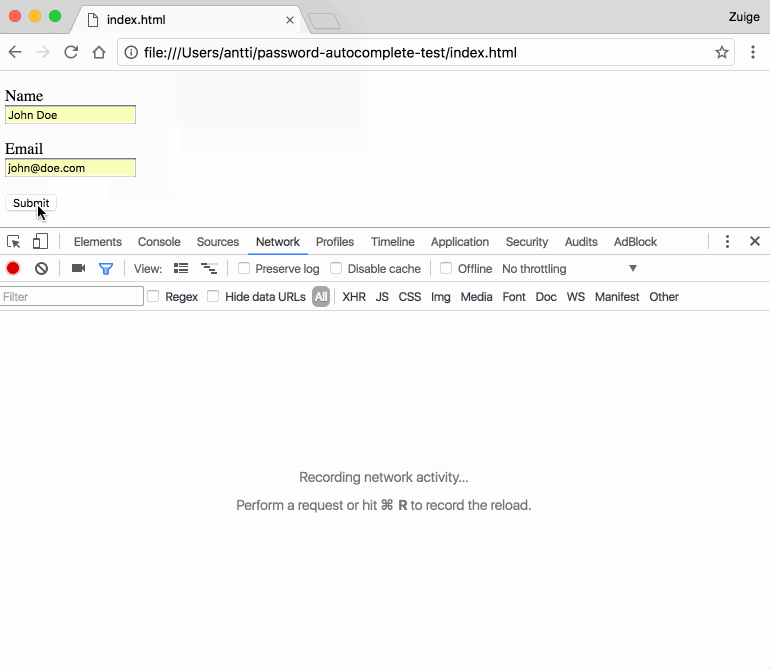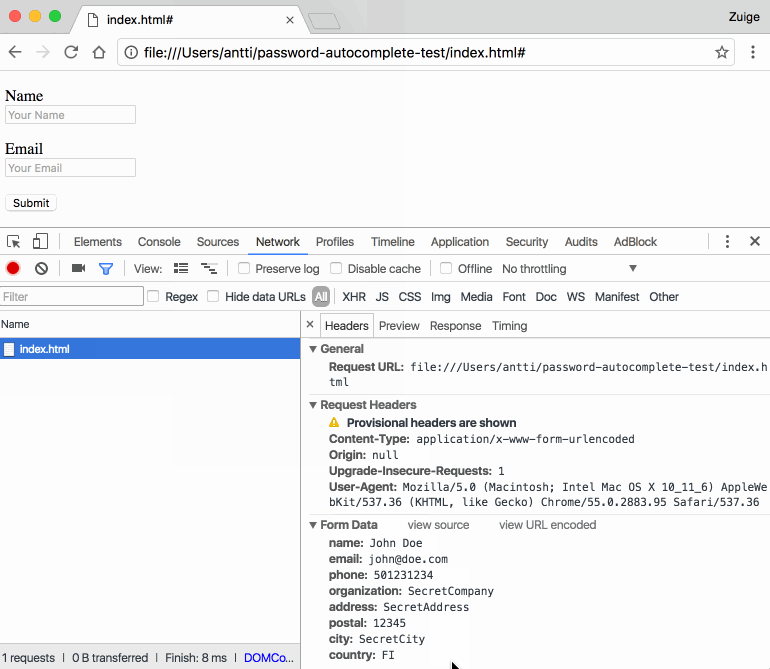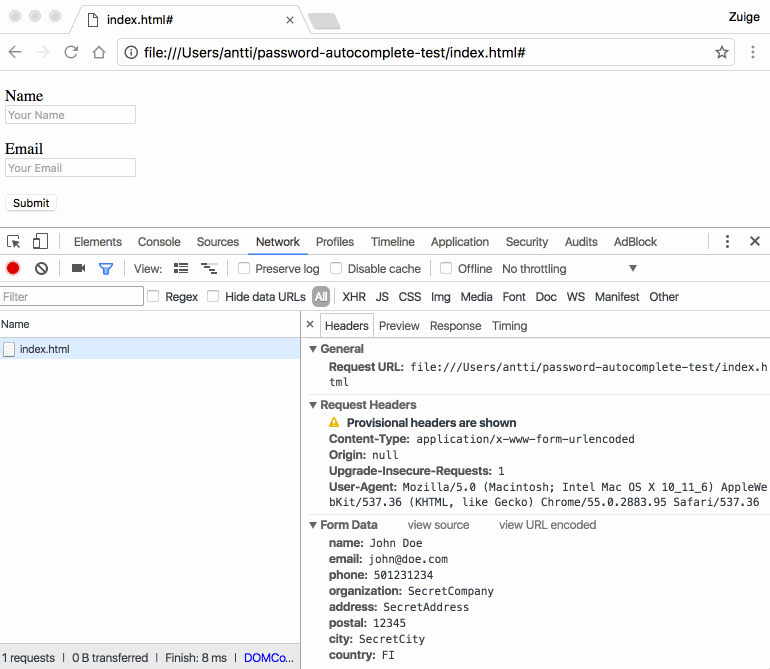
Firefox isn't affected by the issue because it requires manual autofill for text boxes --- you have to click or hover over a text box before it's filled in. Chrome, Safari and Opera are all vulnerable to the phishing attack as well as standalone password managers offering form autofill like LastPass.
One seemingly easy fix would be to restrict autofill to only visible boxes or move to Firefox's manual autofill method. In the meantime you should be extra careful where you use the feature or disable it altogether.
