The big picture: Researchers from Microsoft's Threat Protection Intelligence Team are working with Intel Labs to further explore the use of deep learning to help fight malware. Through static analysis, most threats can be caught before they can even run.
Building on an earlier joint effort, the two are now attempting to tackle malware classification as a computer vision task through an approach known as static malware-as-image network analysis (STAMINA). By plotting malware binaries as grayscale images, textural and structural patterns can be analyzed and identified as either benign or malicious.
To do this, malware binaries were converted into two-dimensional images which involved pixel conversion, reshaping and resizing. Each byte was given a value between 0 and 255, corresponding to pixel intensity. The file size was then used to determine the width and height of an image, transforming it into a two-dimensional picture.
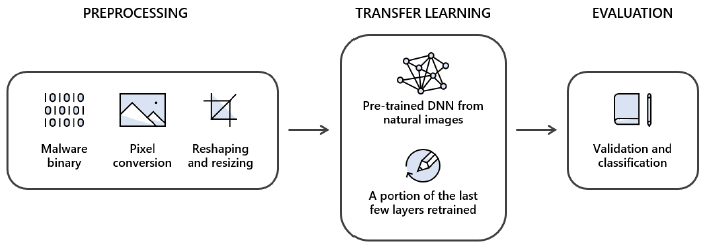
Across 2.2 million portable executable (PE) binaries (temporally split 60:20:20 for training, validation and testing), the approach achieved a recall of 87.05 percent at 0.1 percent false positive rate and 99.66 percent recall and 99.07 percent accuracy at 2.58 false positive rate overall.
For more complex threats, static analysis can be used in conjunction with dynamic and behavior analysis to build even more comprehensive threat detection systems.
Masthead credit: Yuttanas