Editor's take: Ransomware attacks in recent years have proven that no company is safe from them, which has encouraged hacker groups like DarkSide to grow their ambitions and go after larger targets. Unfortunately for them, this also prompted a fierce response from government agencies – something they likely didn't expect or plan for. Still, there are voices in the security community that say this is merely an "exit scam," where ransomware operators retreat for a while to plan for their future attacks.
Earlier this month, a hacker group named DarkSide launched a ransomware attack against the business network of the Colonial Pipeline, forcing the company to shut down the 5,500-mile main pipeline and leading to fuel shortages in 17 states and Washington DC last week.
According to a Bloomberg report, Colonial paid 75 Bitcoin (around $5 million on the day of the transaction) in ransom to the Eastern European hackers, but officially the company has maintained a different narrative of not having any intention of paying the extortion fee in cryptocurrency, as the DarkSide group had demanded. However, the Georgia-based company is said to have made the payment within hours of the attack, possibly using a cyber insurance policy to cover it.
Once the payment was received, the hackers provided Colonial with a decryption tool for the restoration of its IT systems. However, the process was so slow that the company simply resorted to using its own backups to speed up the recovery. The fuel shipments were eventually resumed on Wednesday evening, but the story triggered a massive government response, including an executive order signed by President Joe Biden for the strengthening of US cybersecurity defenses.
Blockchain analytics firm Elliptic claims to have traced the wallet used by DarkSide for receiving ransom payments. The company found the wallet had been active since early March, and has received 57 payments from 21 different wallets, which seem to match known ransoms that have been paid over the last two months.
The transactions total is estimated at $17.5 million, and Elliptic was also able to trace where DarkSide is sending some of its funds. What it found was the group is using several exchanges, as well as a darknet marketplace called Hydra that is popular among Russian cybercriminals.

Earlier this week, DarkSide released an apology on the dark web explaining that it never intended to cause any "problems for society." Now, the group claims it has lost control over its web servers as well as a significant part of its funds. Specifically, the servers were seized by an unknown entity and at least one of its main accounts, which was used to pay its core group and affiliates who carried the attacks, has been drained.
Some speculate this was the result of swift, coordinated action from US authorities with help from the Russian government, as there have been suspicions that DarkSide operates in Russia. However, experts from security firms Emsisoft, FireEye and Intel 471 explain this is simply an "exit scam," an otherwise typical behavior used by ransomware operators as a way to hide their tracks and retreat in the shadows where they can plot their next move, sometimes under a different name.
The second explanation is the most plausible one, as other ransomware have made similar announcements in the wake of increased media spotlight given to their recent operations. For instance, REvil and Avaddon said they would stop advertising their Ransomware-as-a-Service platforms and "go private." Additionally, they plan to stop attacking critical infrastructure such as healthcare and educational institutions, energy grids, fuel pipelines, and anything else that would attract the kind of attention that resulted from the recent DarkSide attack on the Colonial Pipeline.
Colonial was not the only company targeted by DarkSide – Toshiba said in a statement on Friday the European side of its business had been hit by a ransomware attack on May 4. It didn't pay a ransom, since the stolen data did not include sensitive information thanks to swift action that prevented the attackers from moving horizontally across the company's network systems.
Ireland's health service was also victim to a "significant" and "sophisticated" ransomware attack on its systems, prompting officials to shut down the affected systems as a precaution. Fortunately, the country's Covid-19 vaccination program wasn't directly affected by the attack, but there's been a significant disruption in all other health services as hospitals were forced to work offline.
In Germany, chemical distribution company Brenntag paid $4.4 million worth of Bitcoin in ransom to DarkSide to protect its operations at over 670 sites and 150 gigabytes of sensitive information. The company's network was infiltrated earlier this month with the help of stolen credentials and lax login security that lacked multifactor authentication.
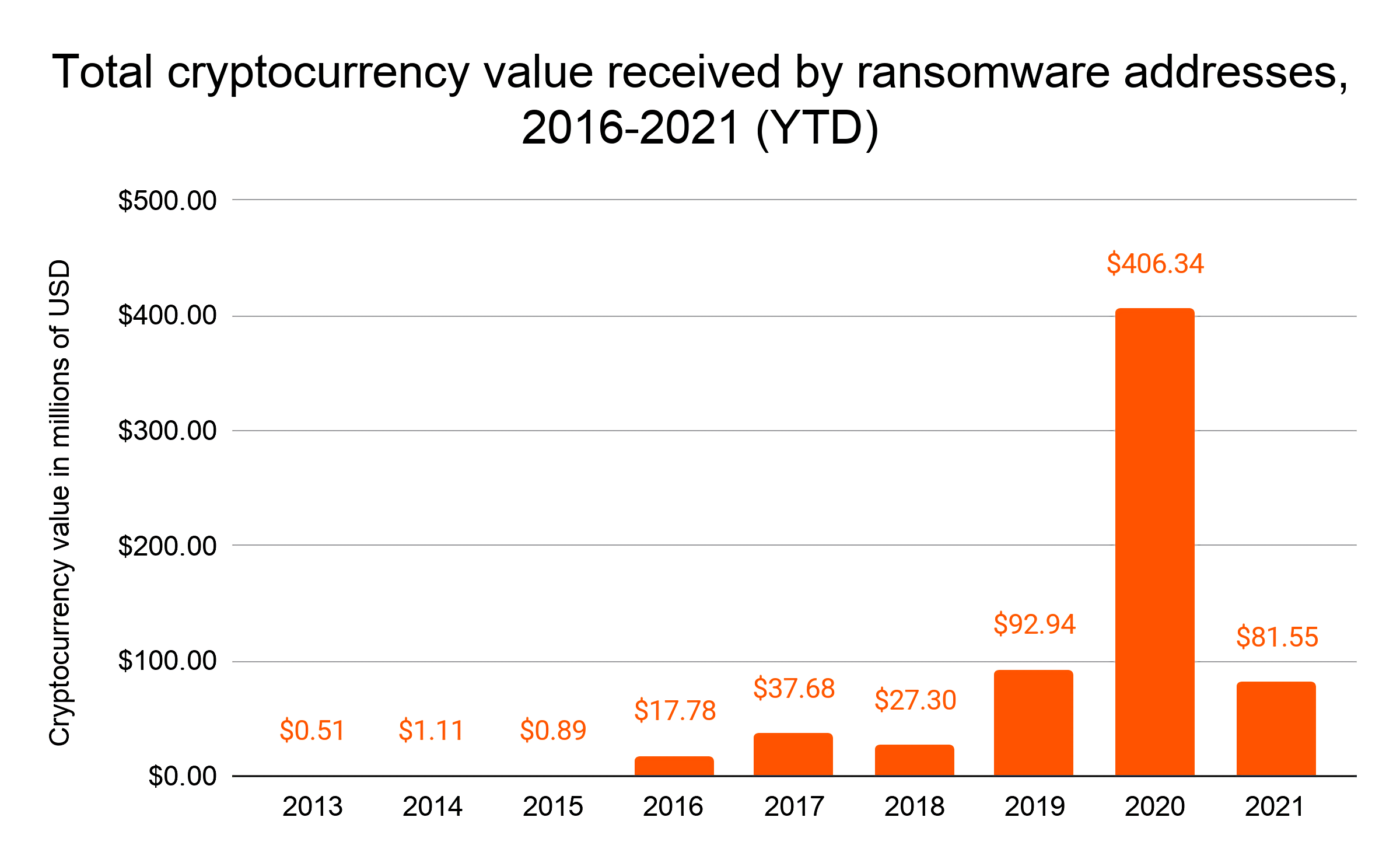
Ransomware-as-a-Service appears to be big business, at least according to figures from Chainalysis, who says that ransomware attacks exploded last year and are showing no signs of slowing down. In the first months of 2021, victims paid in excess of $81 million, a huge chunk of which went to DarkSide.
Another interesting observation is that for the past eight years, ransomware operators have been moving their funds through mainstream exchanges and cryptocurrency tumblers, the latter being used to essentially obscure the source address for transactions. This makes it very attractive for money laundering, frauds, and other criminal activities.
Last month, US authorities arrested Roman Sterlingov, the operator of a cryptocurrency tumbler called Bitcoin Fog that allegedly laundered $335 million worth of Bitcoin since 2011. This week, the DOJ and IRS started investigating Binance, the world's largest cryptocurrency exchange by volume, but the latter has yet to be accused of any wrongdoing.
The main issue with ransomware attacks is the difficulty of catching the people responsible for them, as some of them reside in countries that can be described as cybercrime safe havens. A notable example is North Korea, which is said to have used cryptocurrency experts and hackers to steal billions of dollars, aiding its military ambitions and allowing it to evade US sanctions.
Another problem is the high mobility of these malicious actors, something that calls for a global, concerted effort if we want there to be any significant change in the proliferation of ransomware attacks. The UN has made the first steps in that direction with a proposal for countries to sign on a set of rules akin to a "Digital Geneva Convention," but there's been little progress on that front.
