TL;DR: Twitter acknowledged a data breach that may have unmasked pseudonymous user accounts. While it didn't float any actual numbers, previous reports indicated a vulnerability exposed more than 5.4 million Twitter IDs and associated phone numbers and email addresses. Twitter patched the security hole in January, but a "bad actor" claims he used it the month before to scrape the data.
Last week, Twitter confirmed that hackers had compromised some accounts on its platform. Developers created the flaw with a June 2021 update for its Android client, that allowed a bad actor to associate user accounts with email addresses and phone numbers. Twitter learned of the vulnerability through its bug bounty program in January 2022 and patched it immediately thinking that nobody had been affected.
However, last month BleepingComputer reported it had found a database on a hacker forum containing the phone numbers and email addresses associated with over 5.4 million Twitter accounts.
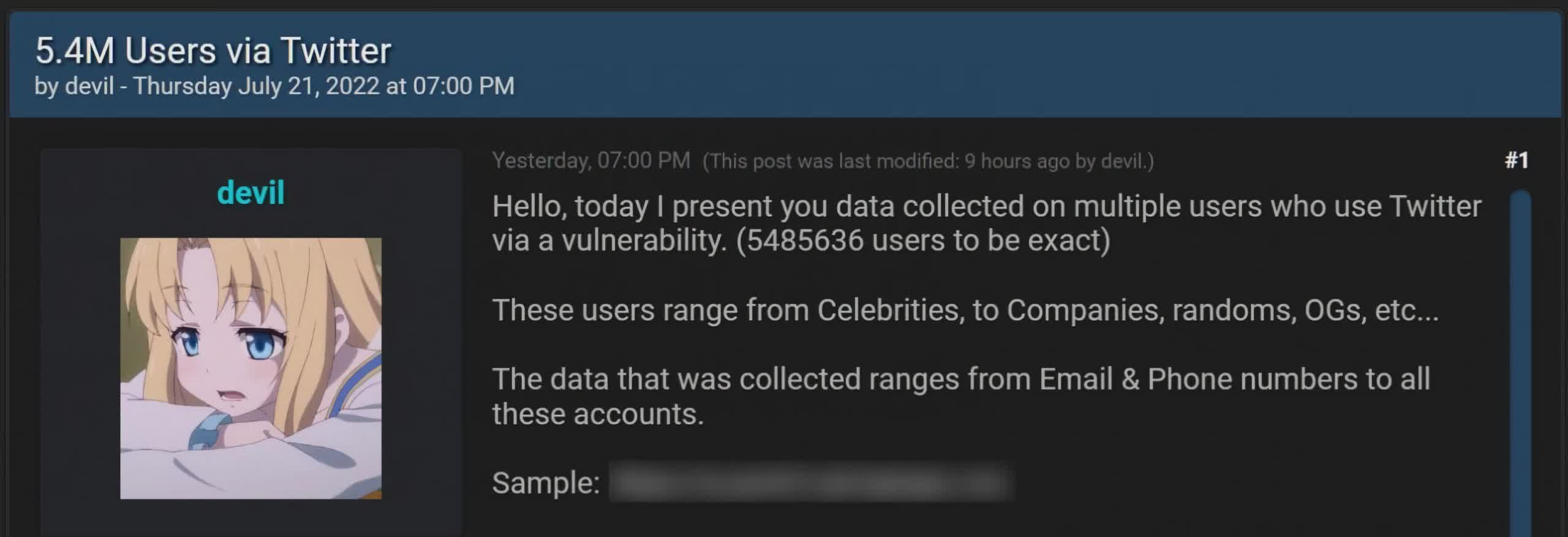
"Hello, today I present you data collected on multiple users who use Twitter via a vulnerability. (5485636 users to be exact)," the hacker who calls himself "devil" said in his post. "These users range from Celebrities, to Companies, randoms, OGs, etc [sic]."
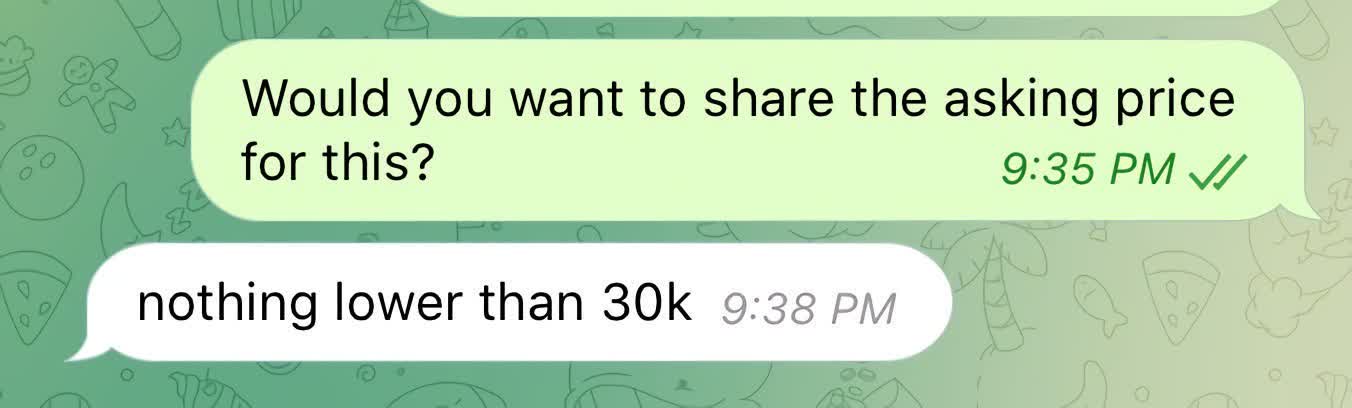
Restore Privacy notes that devil wants to get at least $30,000 for the stolen data and said that he'd already had some bites from interested parties.
A security researcher and bug bounty hunter going by "zhirinovskiy" says the flaw lets anyone obtain the Twitter ID of any user by submitting a phone number/email. The exploit works even if a user's account is set to be undiscoverable in the settings. It also requires no authentication --- just a handful of code.
"The bug exists due to the proccess of authorization used in the Android Client of Twitter," zhirinovskiy said, who reported the flaw through HackerOne. "Specifically in the procces of checking the duplication of a Twitter account [sic]."
Essentially, devil would feed the system phone numbers or emails and it would return whether those were associated with Twitter IDs. From there it's a fairly straightforward matter to create a profile from publicly available posts and other information.
Zhirinovskiy reported the flaw to Twitter on January 1, and developers issued a fix on January 13. However, devil claims he collected the data in December 2021 before it was patched. Some have suggested that devil and zhirinovskiy are the same person and that he is trying to cash out on both ends. Devil denies these allegations with almost too much vigor --- as if he has something to hide.
"I don't want to white hat in trouble who reported it on H1 [sic]," he told BleepingComputer. "I guess a lot of people are trying to connect him to me, I would be pissed if I was him. So I cant stress this enough I have nothing to do w him nor H1."
Twitter's confirmation does not indicate the number of compromised user accounts, but it is pretty clear we're dealing with the same vulnerability that zhirinovskiy reported and devil exploited. The company said that it would notify affected users, presumably through their now exposed email address. It particularly noted anonymous accounts.
"If you operate a pseudonymous Twitter account, we understand the risks an incident like this can introduce and deeply regret that this happened. To keep your identity as veiled as possible, we recommend not adding a publicly known phone number or email address to your Twitter account."
Although passwords were not compromised, Twitter advises any users with concerns to use two-factor authentication apps or hardware security keys to protect their accounts.
Image credit: Forum Post by BleepingComputer, Devil Chat by Restore Privacy
