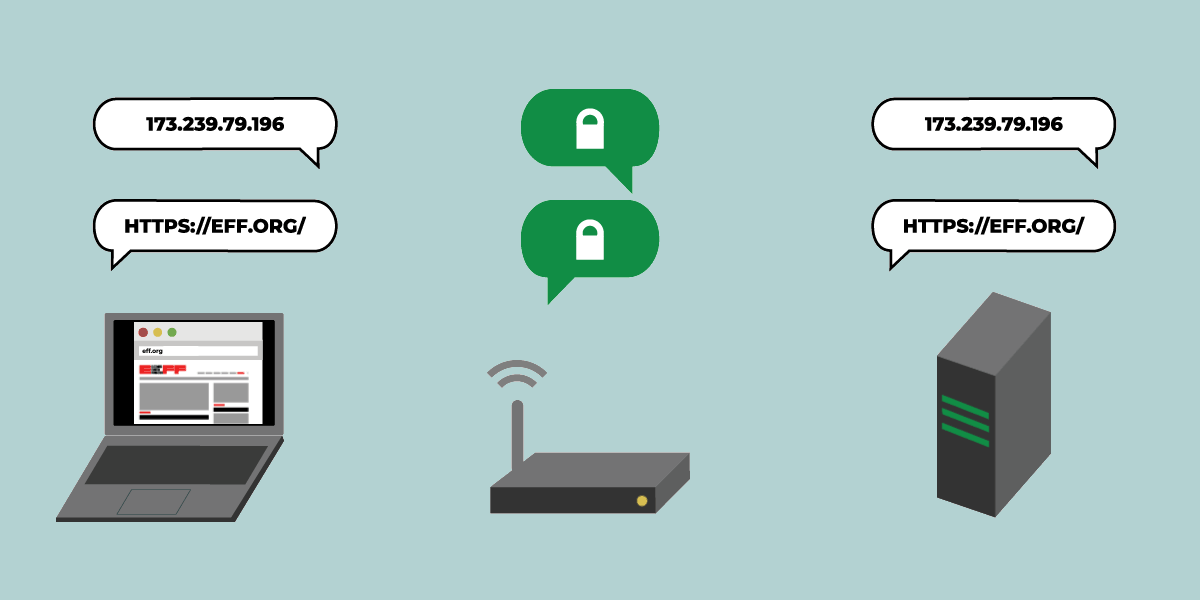
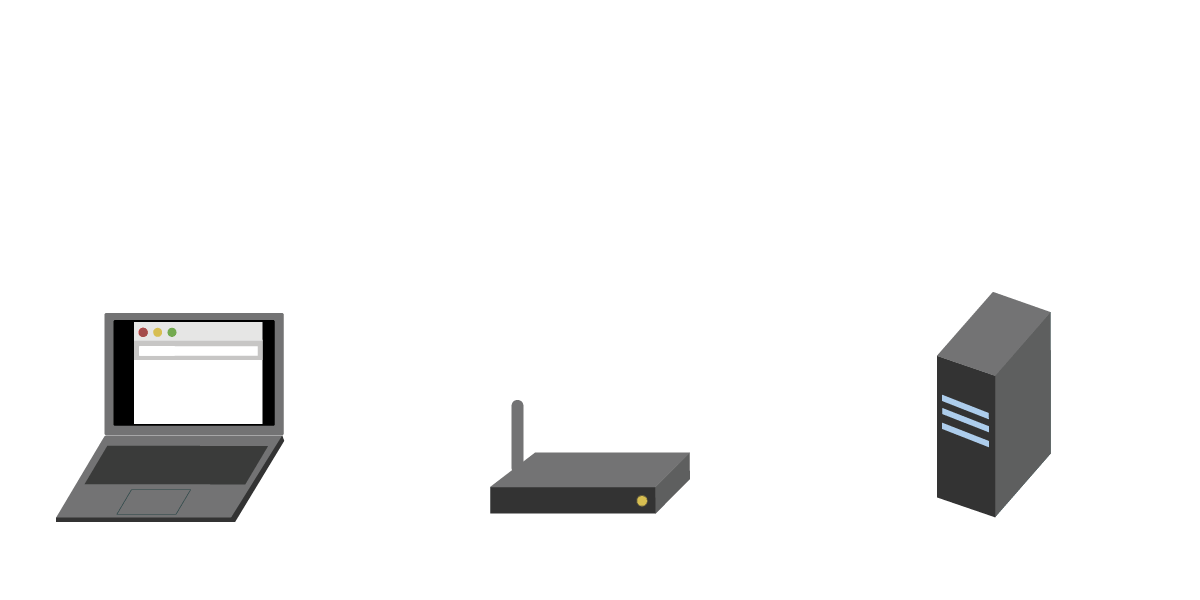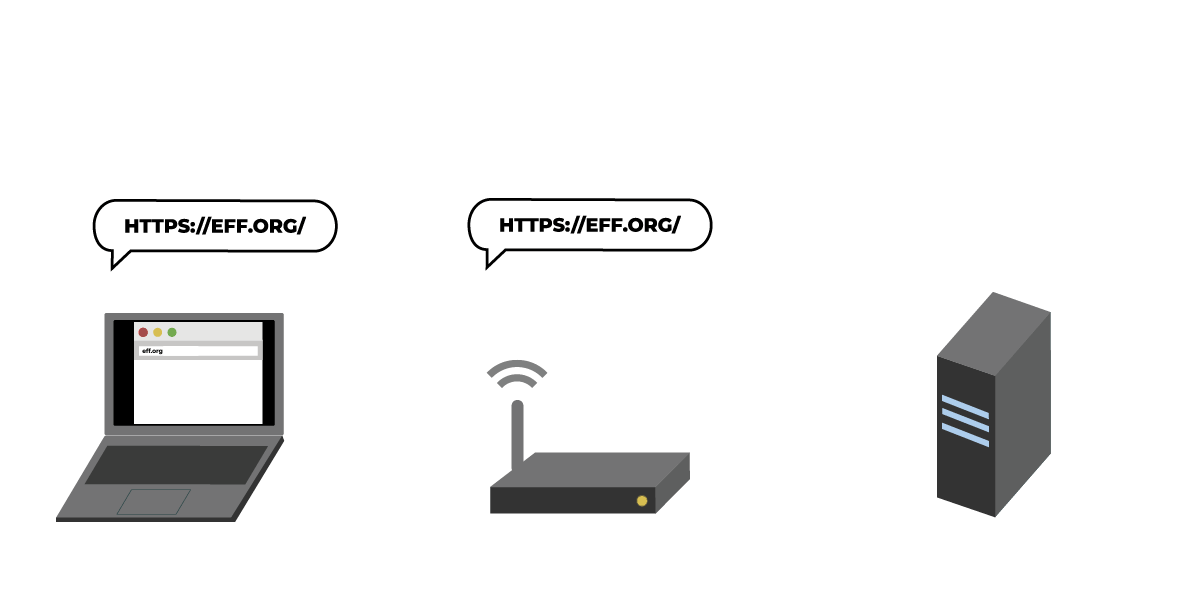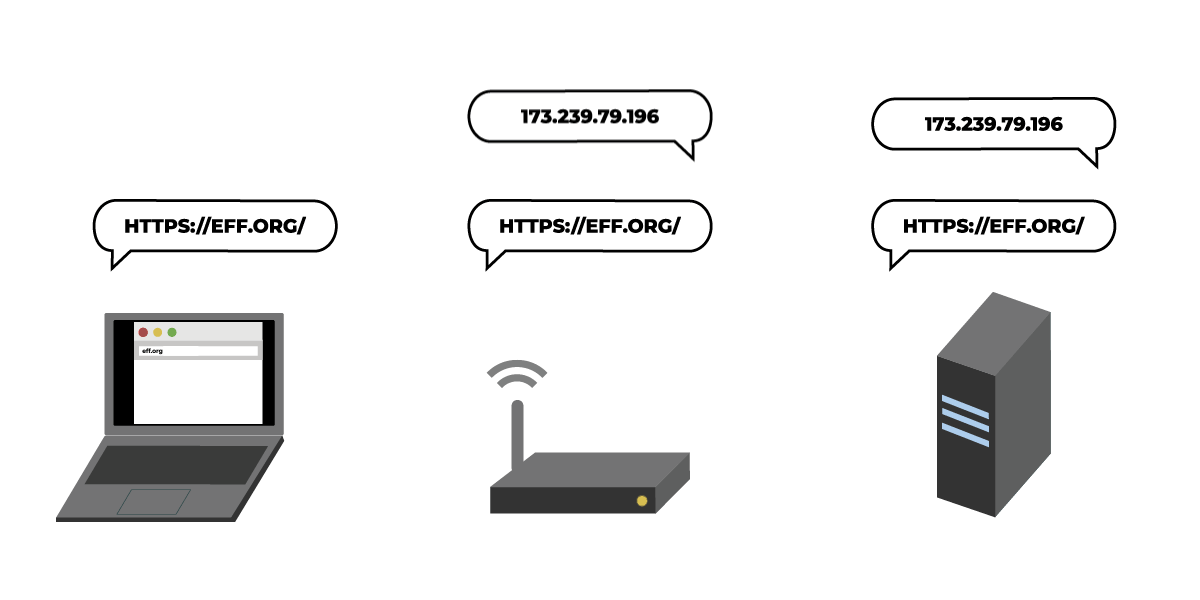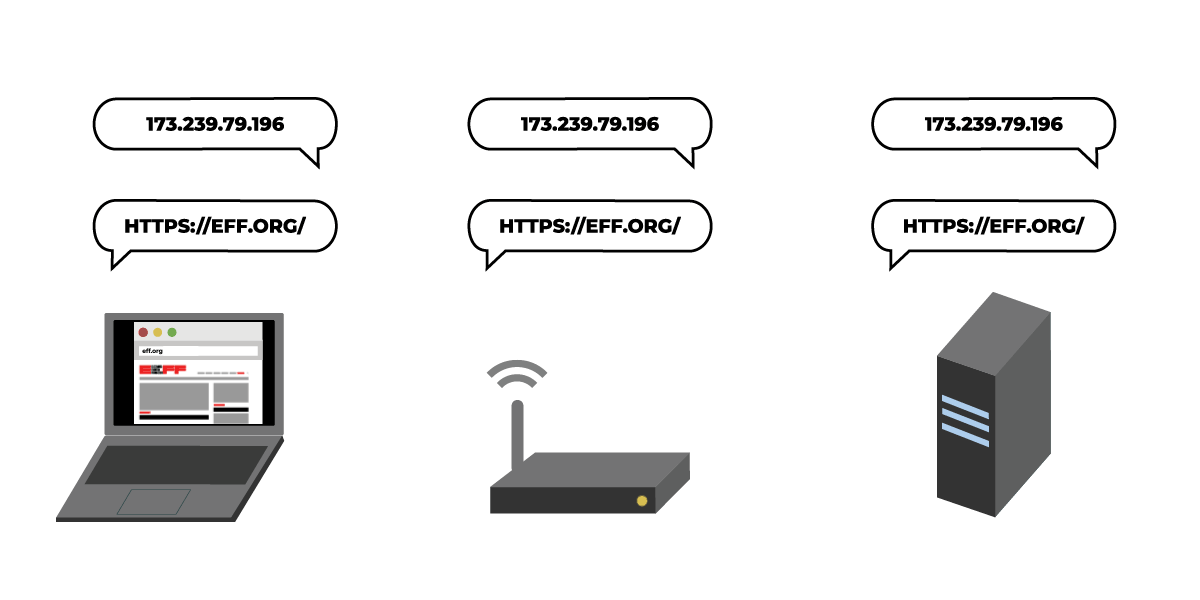
Thanks to the success of projects like Let’s Encrypt and recent UX changes in the browsers, most page-loads are now encrypted with TLS. But DNS, the system that looks up a site’s IP address when you type the site’s name into your browser, remains unprotected by encryption.
Editor’s Note:
Guest author Max Hunter is the Engineering Director at EFF. Max's team of engineers maintain Certbot, STARTTLS Everywhere, and other projects to encrypt the Internet. Max also serves on the board of the Internet Security Research Group.
Because of this, anyone along the path from your network to your DNS resolver (where domain names are converted to IP addresses) can collect information about which sites you visit. This means that certain eavesdroppers can still profile your online activity by making a list of sites you visited, or a list of who visits a particular site. Malicious DNS resolvers or on-path routers can also tamper with your DNS request, blocking you from accessing sites or even routing you to fake versions of the sites you requested.
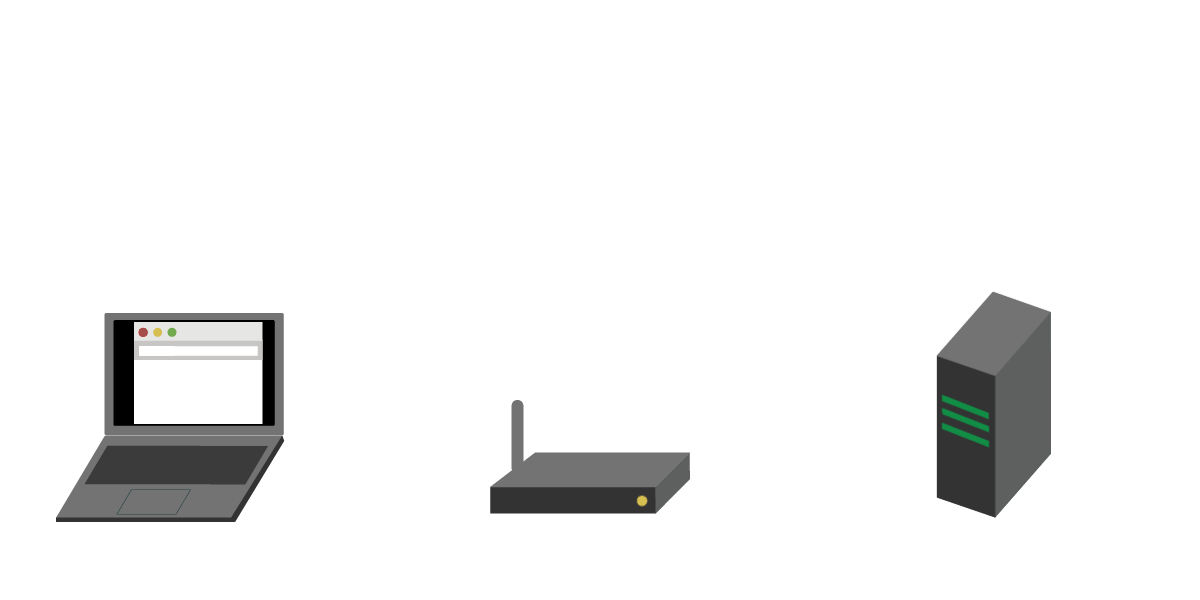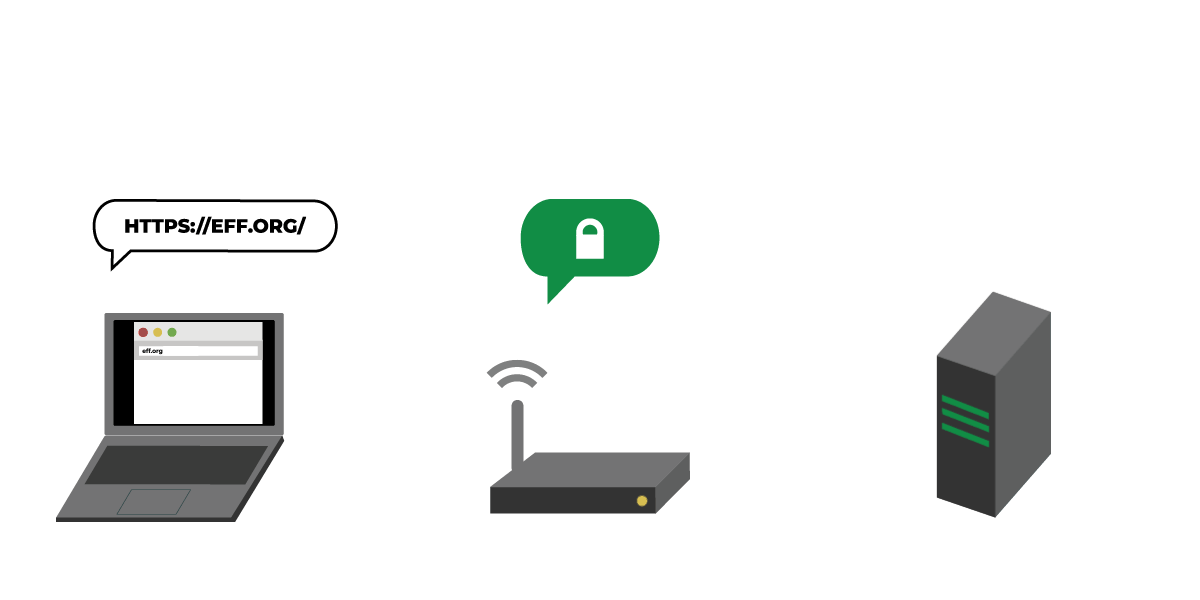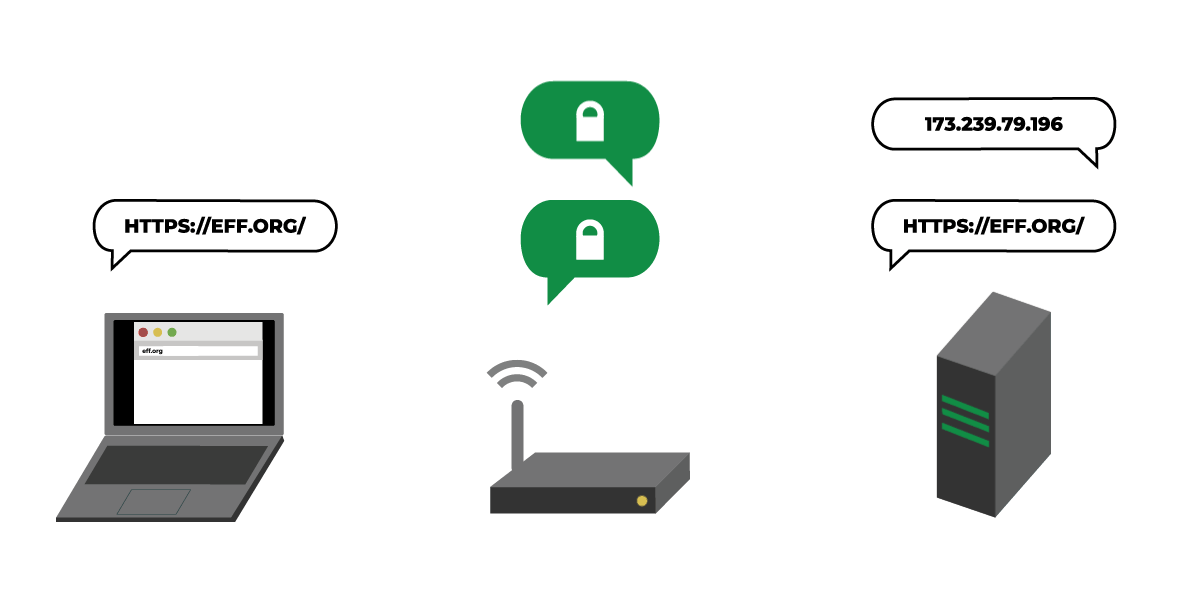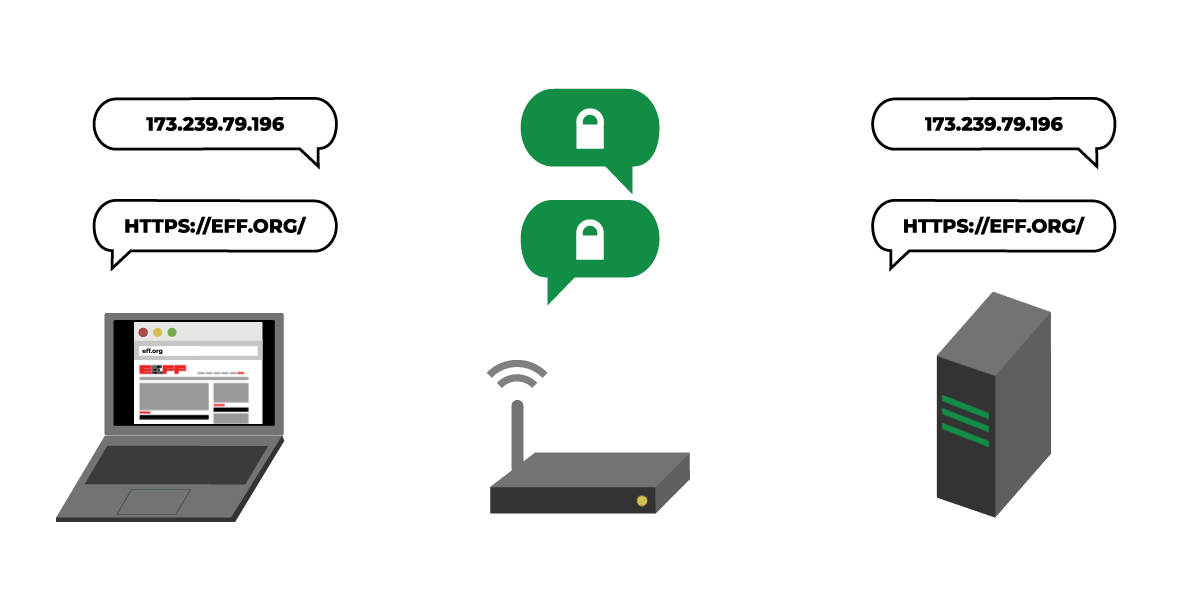
A team of engineers is working to fix these problems with “DNS over HTTPS” (or DoH), a draft technology under development through the Internet Engineering Task Force that has been championed by Mozilla. DNS over HTTPS prevents on-path eavesdropping, spoofing, and blocking by encrypting your DNS requests with TLS.
Alongside technologies like TLS 1.3 and encrypted SNI, DoH has the potential to provide tremendous privacy protections. But many Internet service providers and participants in the standardization process have expressed strong concerns about the development of the protocol. The UK Internet Service Providers Association even went so far as to call Mozilla an “Internet Villain” for its role in developing DoH.
ISPs are concerned that DoH will complicate the use of captive portals, which are used to intercept connections briefly to force users to log on to a network, and will make it more difficult to block content at the resolver level. DNS over HTTPS may undermine plans in the UK to block access to online pornography (the block, introduced as part of the Digital Economy Act of 2017, was planned to be implemented through DNS).
Members of civil society have also expressed concerns over plans for browsers to automatically use specific DNS resolvers, overriding the resolver configured by the operating system (which today is most often the one suggested by the ISP). This would contribute to the centralization of Internet infrastructure, as thousands of DNS resolvers used for web requests would be replaced by a small handful.
That centralization would increase the power of the DNS resolver operators chosen by the browser vendors, which would make it possible for those resolver operators to censor and monitor browser users’ online activity. This capability prompted Mozilla to push for strong policies that forbid this kind of censorship and monitoring. The merits of trusting different entities for this purpose are complicated, and different users might have reasons to make different choices. But to avoid having this technology deployment produce such a powerful centralizing effect, EFF is calling for widespread deployment of DNS over HTTPS support by Internet service providers themselves. This will allow the security and privacy benefits of the technology to be realized while giving users the option to continue to use the huge variety of ISP-provided resolvers that they typically use now. Several privacy-friendly ISPs have already answered the call. We spoke with Marek Isalski, Chief Technology Officer at UK-based ISP Faelix, to discuss their plans around encrypted DNS.
Supporting privacy-protecting technologies is a moral imperative.
Faelix has implemented support for DNS over HTTPS on their pdns.faelix.net resolver. They weren’t motivated by concerns about government surveillance, Marek says, but by ”the monetisation of our personal data.” To Marek, supporting privacy-protecting technologies is a moral imperative. “I feel it is our calling as privacy- and tech-literate people to help others understand the rights that GDPR has brought to Europeans,” he said, “and to give people the tools they can use to take control of their privacy.”
EFF is very excited about the privacy protections that DoH will bring, especially since many Internet standards and infrastructure developers have pointed to unencrypted DNS queries as an excuse to delay turning on encryption elsewhere in the Internet. But as with any fundamental shift in the infrastructure of the Internet, DoH must be deployed in a way that respects the rights of the users.
Browsers must be transparent about who will gain access to DNS request data and give users an opportunity to choose their own resolver. ISPs and other operators of public resolvers should implement support for encrypted DNS to help preserve a decentralized ecosystem in which users have more choices of whom they rely on for various services. They should also commit to data protections like the ones Mozilla has outlined in their Trusted Recursive Resolver policy. With these steps, DNS over HTTPS has the potential to close one of the largest privacy gaps on the web.
This article was originally published on EFF.org. Republished with permission.
https://www.techspot.com/news/82061-eff-encrypted-dns-could-help-close-biggest-privacy.html