In brief: Most non-tech savvy web users presume that a padlock in the browser bar means a site is legitimate and safe, but that’s far from the reality. New research shows a massive 49 percent of all phishing sites used Secure Sockets Layer protection, and by extension showed the padlock, as of Q3 2018.

Google has spent years trying to get more of the web to adopt the HTTPS protocol, in which is data is encrypted using SSL/TLS as it travels between browser and website. Many still believe the presence of a padlock equals trustworthiness, but an increasing number of phishing sites are displaying it.
According to new data from PhishLabs (via Krebs on Security), the 49 percent of phishing websites using SSL is up from 35 percent during the last quarter and 25 percent a year ago. The increase has been put down to the number of phishers who are registering their own domain names and creating certificates for them, as well as Chrome displaying ‘Not Secure’ on sites that lack encryption. Certificate authorities aren’t able to check every site to ensure its legitimacy and many that request these certificates don’t have any content on them at the time.
Back in December last year, a poll carried out by PhishLabs showed that more than 80 percent of responders believed the padlock indicated that a website was either legitimate and/or safe, neither of which is true.
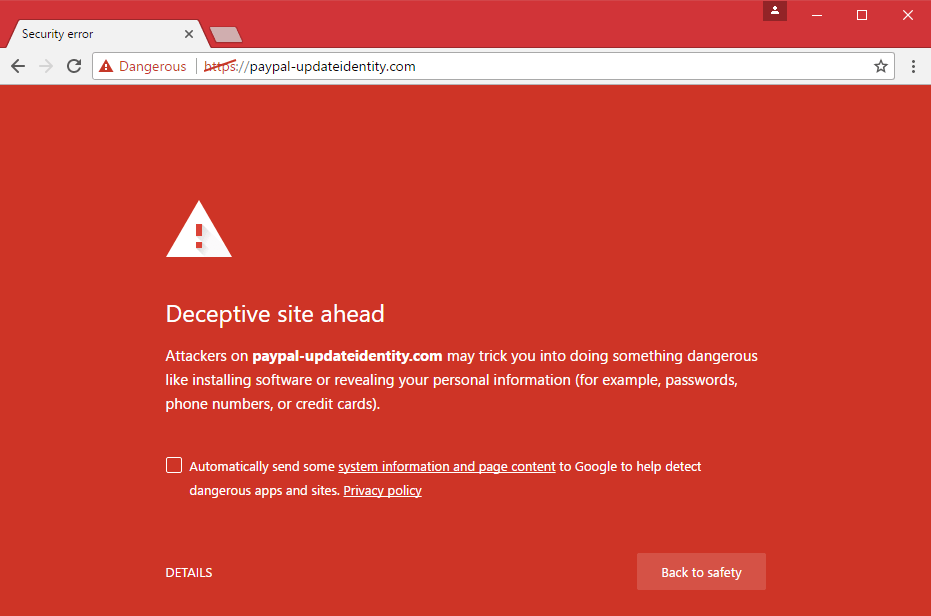
Browser makers are fighting back by working with security firms to identify and block new phishing sites, but some manage to evade being flagged. The safest option is to not input your details if you have any suspicions about a website, even if it does have a padlock.
https://www.techspot.com/news/77585-half-all-phishing-sites-display-padlock-making-people.html