
Intel this week announced they have issued firmware updates for 90 percent of their CPUs launched in the past five years. These updates help protect against the Meltdown and Spectre vulnerabilities which could allow hackers to view sensitive information on your computer. Most CPUs released in the past five to 10 years are vulnerable.
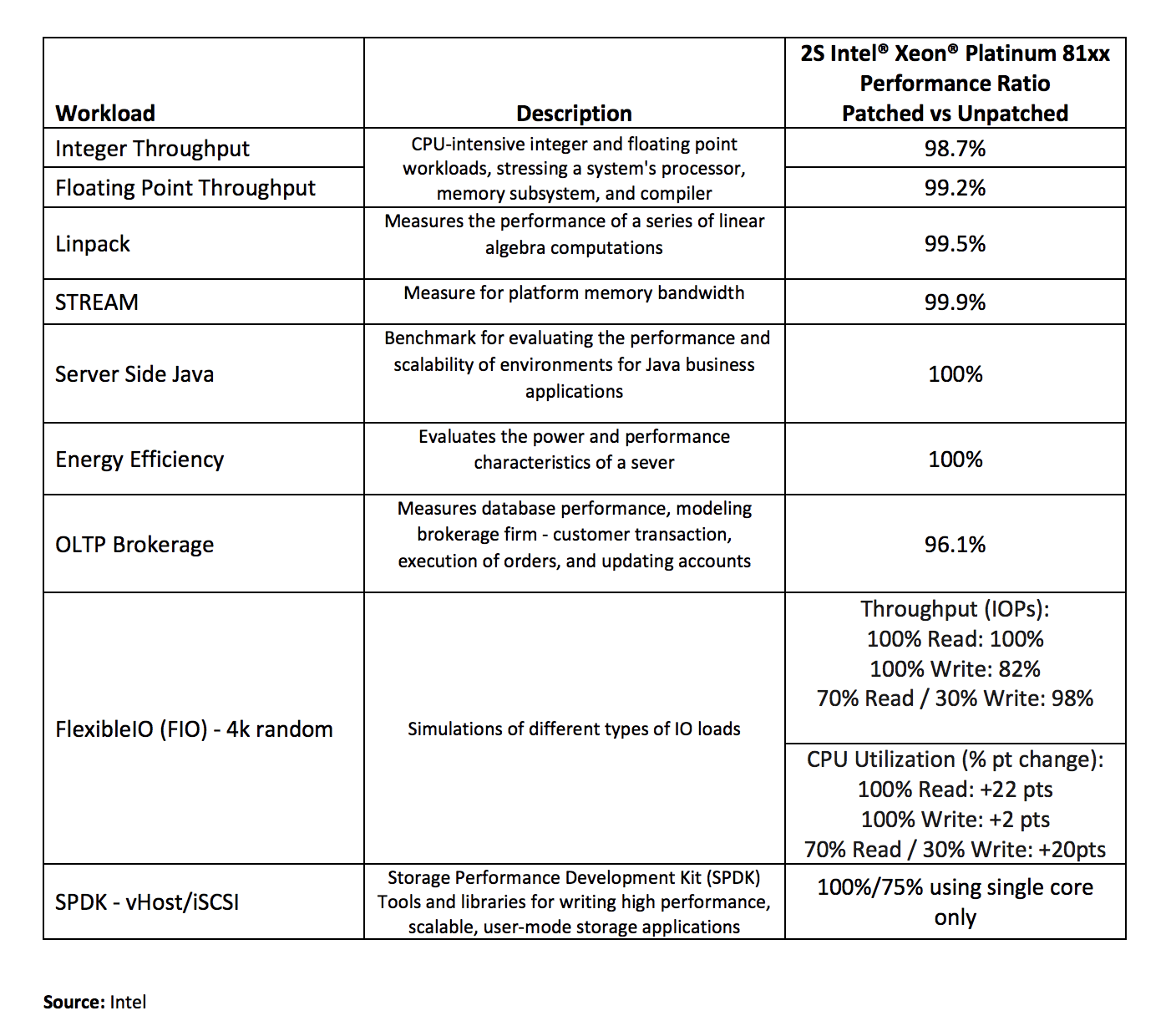
In addition to Intel, many other software and hardware vendors have also released patches for their systems. Based on their data center benchmarks, Intel has shown an overall zero to two percent performance impact on systems that have received the patch. Storage performance may be hindered even more with some tests showing up to "an 18 percent decrease in throughput performance." Single-core performance in storage performance development kit (SPDK) tests was affected by as much as 25 percent.
For reference, you can check out TechSpot's performance tests that include consumer-grade productivity tests and gaming.
There is still much more work to do, though. The patches have been well received but Intel recently admitted that they are causing more frequent and unwanted system reboots. The company has said they have started addressing the reboot issue and the specific use cases that saw the greatest performance hit.
Furthermore, once Intel issues these patches and microcode updates, it doesn't automatically translate in safety for actual users and businesses. Part of the vulnerabilities (Meltdown) can be patched at the OS level, while Spectre requires a lower-level update, often delivered via a motherboard BIOS update. It's hard to predict how many machines will remain vulnerable based on users who simply won't update, leaving the door open for exploits when and if those come. As a side note, a new utility released by security expert Steve Gibson called InSpectre lets you check if your computer is vulnerable to either flaw with ease.
There are rumors of two new attacks called Skyfall and Solace although they cannot be verified yet. Security researchers are claiming they are still under NDA to allow manufacturers to address the issues. Until more clarification is released, this may just be the case of people trying to hop on the vulnerability-frenzy bandwagon.
Regardless of whether or not these Bond-inspired attacks turn out to be real or not, we are not out of the woods yet.
https://www.techspot.com/news/72830-intel-90-percent-cpus-have-received-spectre-meltdown.html