Facepalm: Meta recently implemented a centralized login system to make it easier for Instagram, Facebook, and Meta (VR) users to manage their accounts. Unfortunately, in setting up the 2FA system, engineers overlooked a glaring failure regarding attempt limitation.

A freshman security researcher named Gtm Mänôz noticed the bug in July 2022. While looking for his first bug bounty to present at BountyCon 2022, Mänôz started playing around with the Meta Accounts Center interface, which manages all Meta accounts, adding similar functionality as Google's one-stop login for its various services (YouTube, Gmail, Docs, etc).
He noted that the page allowed users to associate a phone number with their accounts when linking them. Users simply enter their phone number and then the six-digit 2FA code the system sends them. However, Mänôz discovered that if the wrong code is entered, the Account Center just asks the user to reinput it instead of sending a new code.
Furthermore, there was no limit on how many failed attempts one could enter into the verification box. This oversight allowed Mänôz to brute force the 2FA on his own account to associate his phone number with another Facebook profile. The only warning comes after the phone number is stolen in an email from Meta to the victim informing them that it has been linked to another user's account.
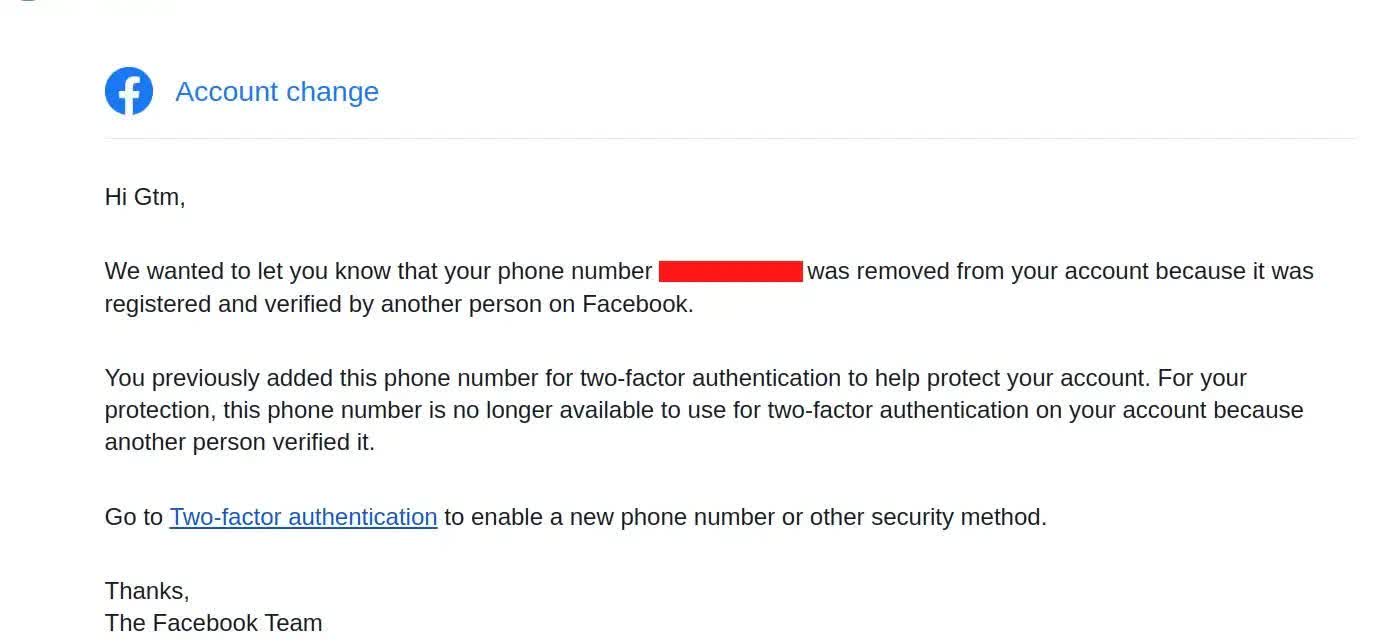
While the harmfulness of this exploit is mainly limited to a bothersome re-establishing of the owner's phone number, it effectively disables 2FA on the victim's account, albeit temporarily. Until the target takes action, they are open to password phishing attacks.
"Basically, the highest impact here was revoking anyone's SMS-based 2FA just knowing the phone number," Mänôz told TechCrunch.
Mänôz notified Meta of the bug in September, and it patched the vulnerability immediately. A spokesperson said that when Mänôz found the problem, the Meta Accounts Center was still in beta and only available to a small number of users. The representative also noted that Meta's investigation revealed no spikes in the usage of that feature, indicating that hackers hadn't exploited it.
Despite the relatively low-treat of the glitch, Meta awarded Mänôz a $27,200 bug bounty. Not too shabby for his first bug hunt.
Meta has stumbled a few times in the last couple of years regarding the login features of its various accounts. In 2021, it caused a mild panic when it logged everyone out of Facebook when reconfiguring the website. Last year, it purposefully locked many users out of their accounts for not enabling "Facebook Protect" by a deadline set by an official Meta email that looked suspiciously like a phishing scam.
https://www.techspot.com/news/97437-meta-awarded-researcher-27200-bug-bounty-glitch-bypassed.html