Why it matters: Microsoft has issued guidance for fixing a serious Secure Boot vulnerability that affects all Windows systems and is actively being exploited in the wild. Normally, this kind of issue would be patched via monthly servicing updates but the Redmond company has chosen a phased approach to reduce the risk of you or your organization ending up with devices that won't boot. The fix will require some manual steps for now, but will be applied automatically on all supported Windows systems starting next year.

Microsoft's latest Patch Tuesday updates are out for Windows 11 and Windows 10 with several fixes for two operating systems. In the case of Windows 11, the KB5026372 cumulative update introduces no less than 20 changes that improve the user experience as well as fixes for 38 security vulnerabilities and three zero-days affecting various Microsoft products.
At the same time, the Redmond company has released an optional security update addressing a vulnerability in Secure Boot that has been exploited in the wild through the BlackLotus UEFI malware, affecting even up-to-date Windows systems. This affects all supported versions of Windows 11 and Windows 10 and is tracked under CVE-2023-24932.
Ironically, the main purpose of Secure Boot is to protect your PC from loading any untrusted code between the time you power it on and the point where Windows takes control. In other words, it is supposed to prevent hackers who gain physical access to your machine from injecting booby-tapped code known as a "bootkit" that modifies the startup process.
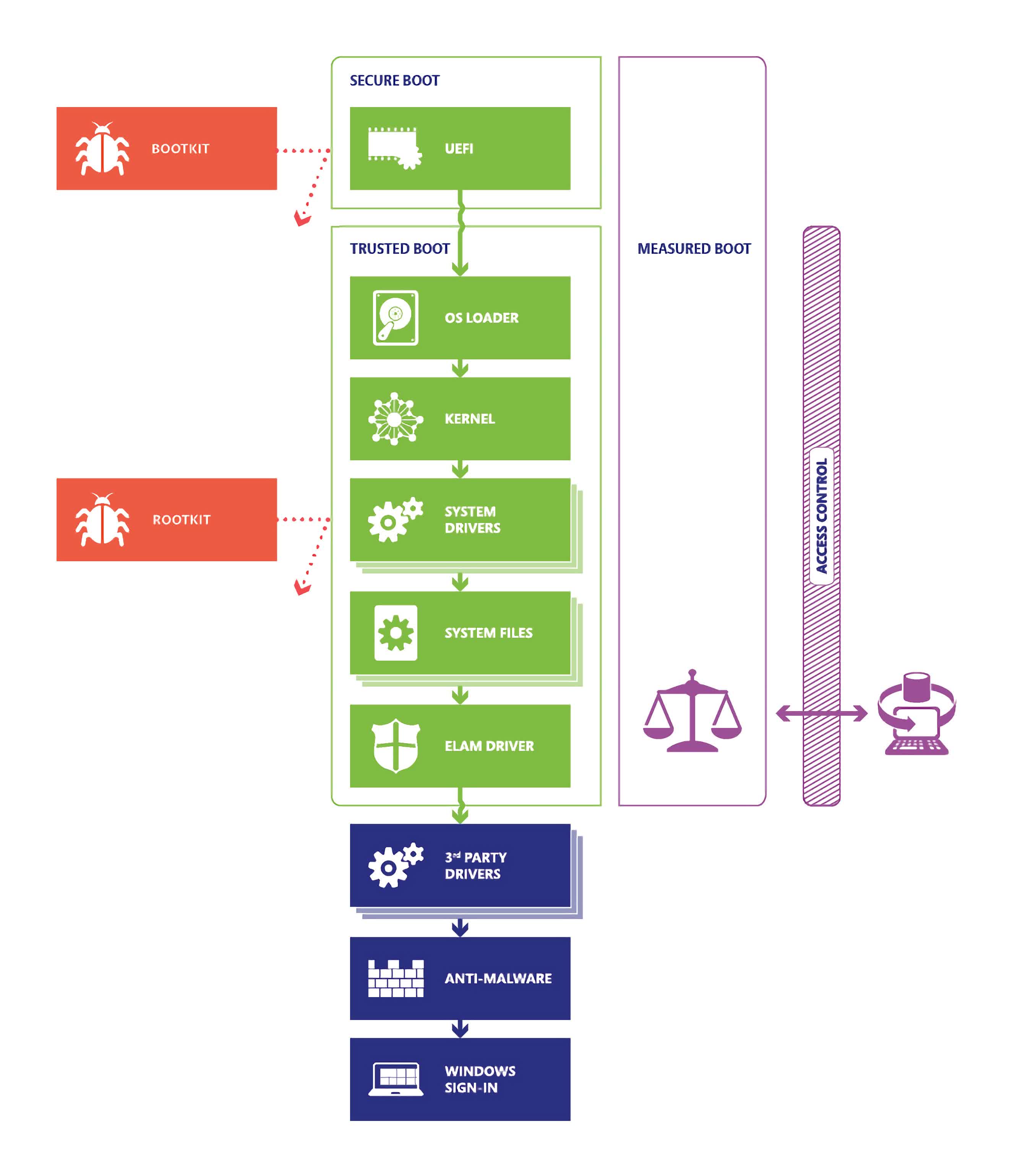
This exploit is known as an "evil cleaner" attack, and allows a malicious actor to introduce malware that can log anything you type and extract it later with very little effort. It can be as simple as booting your machine with a USB drive and letting an automated script do all the work.
Microsoft explains that all Windows systems with Secure Boot enabled are affected by the new flaw, including on-premises devices, virtual machines, and even cloud-based devices. It also affects devices running any major Linux distributions, and we're told a fix is in the works. That said, Microsoft is taking a phased approach to address this vulnerability to minimize disruption and simplify deployment for large organizations.
This means the fix is already present in the latest Patch Tuesday update, but for now it requires some manual steps to enable it:
1. Install the monthly servicing update released on May 9 or later on all of your Windows devices and reboot them before moving on to the next step.
2. Update any bootable media and full backups of Windows you have to ensure they all have the fix for CVE-2023-24932.
3. Apply the Windows Boot Manager revocations to fully protect your systems from attacks that exploit the new vulnerability.
As part of the second phase, Microsoft will release new guidance on July 11, 2023 with simplified update options that achieve the same level of protection against this attack. The final phase will start sometime in the first quarter of 2024, and it will see the fix for CVE-2023-24932 as well as the Windows Boot Manager revocations applied to all supported Windows systems automatically.
It's worth noting that once you deploy all the mitigations for the new flaw on a system, you won't be able to revert those changes. Also, to find out if Secure Boot is enabled on your device, simply open the command prompt and run the "msinfo32," which opens System Information. You should be able to find an entry called "Secure Boot State" in the System Summary section.
Masthead credit: FLY:D