Facepalm: The US military has a serious email situation that has leaked millions of messages from soldiers and top-brass officers. Many of the emails contain sensitive information, including diplomatic documents, tax returns, passwords, and the travel details of high-ranking officials. Even worse, the military has known about the leak for nearly a decade and has done nothing about it.

The problem stems from the similarity of the US armed forces email suffix (.mil) and the country identifier for Mali (.ml). Mali is a country in West Africa, just south of Algeria. Military members and others in the United States frequently mistype .mil as .ml, thus directing emails to the foreign country instead of the military branch they intended to write.
The Financial Times notes that Dutch internet entrepreneur Johannes Zuurbier had a long-standing contract with Mali to manage the country's email traffic. According to Zuurbier, he notified US military officials almost ten years ago that potentially damaging emails were being leaked to Mali. However, nobody seemed to care.
In January 2023, Zuurbier began collecting all misaddressed emails in a last-ditch effort to get anyone of authority in the US to take him seriously because his contract with Mali was ending on July 17. As of last week, he had gathered a cache of almost 117,000 messages, with as many as 1,000 coming in on any given day.
In July, Zuurbier penned another letter to US officials stating, "This risk is real and could be exploited by adversaries of the US."
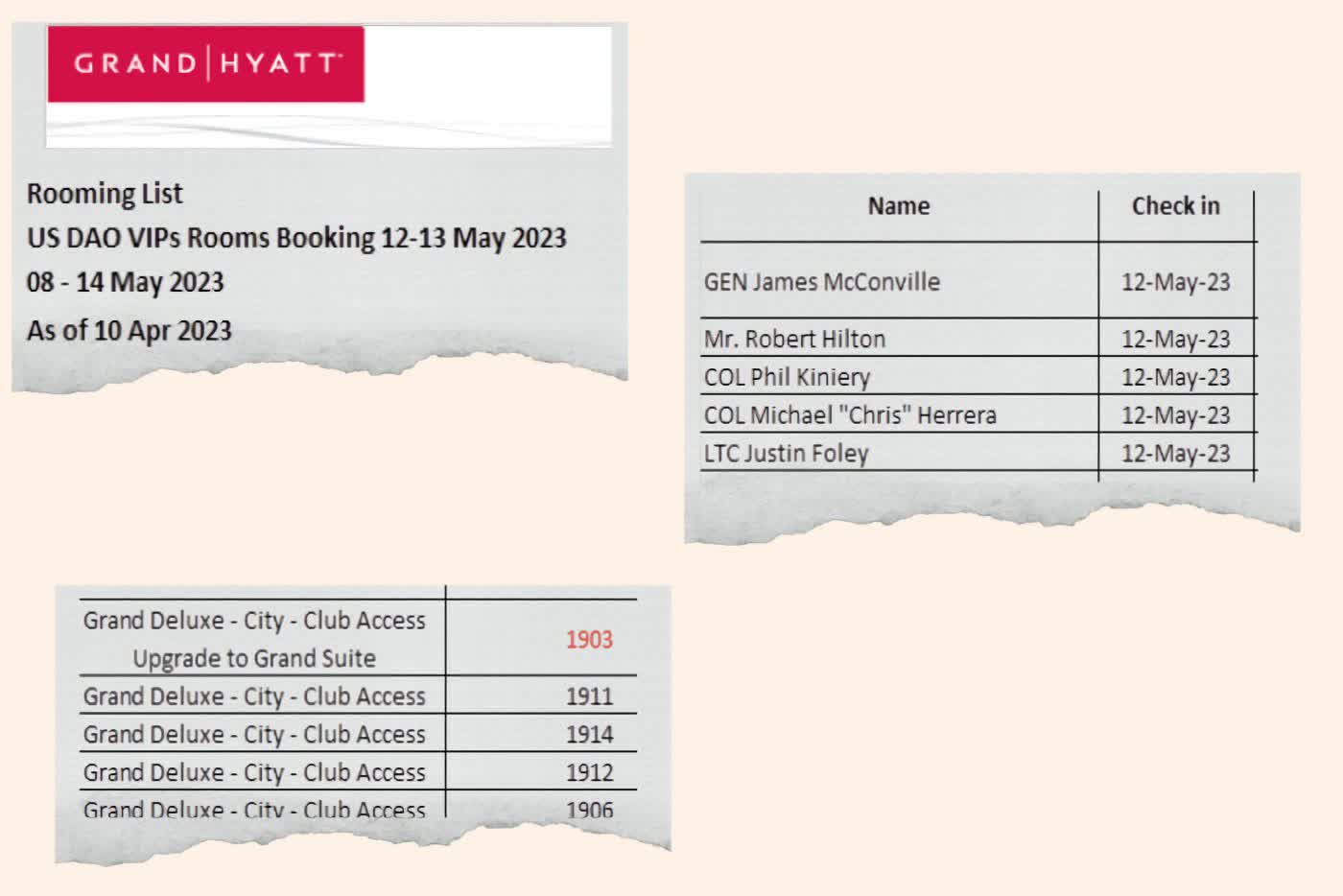
He included examples of sensitive information, including the travel itinerary (above in part) of General James McConville – the US Army's chief of staff. The email had the hotel's name, check-in date, room numbers, and the full names and ranks of McConville and his delegation. Zuurbier hopes that someone in the US government takes heed and fixes the situation. While Zuurbier was above selling the emails to the highest bidder, Mali officials are not guaranteed to be as honest, especially considering the country has close ties with Russia.
To think that thousands of military emails could end up in the hands of a Russian ally is the military definition of SNAFU (situation normal: all f-ed up). However, the problem is of the military's own making since it has ignored Zuurbier's repeated warnings to officials all the way up the chain of command – including the White House.
Although none of the emails were marked "classified," many still had information that could damage individuals or the entire armed services. Examples include X-rays and medical documents, personally identifying information, crew lists for navel vessels, staffing lists for specific bases, maps and photos of installations, criminal complaints and investigations, tax records, internal inquiries, travel itineraries, and contracts.
According to retired Admiral Mike Rogers, who formerly ran the National Security Agency and the US Army's Cyber Command, even this unclassified data greatly benefits an adversary's intelligence gathering.
"If you have this kind of sustained access, you can generate intelligence even just from unclassified information," Roger's told FT, adding, "This is not uncommon. It's not out of the norm that people make mistakes, but the question is the scale, the duration, and the sensitivity of the information."

An FBI agent often mistyped his email address when sending himself notes, including a Turkish embassy alert regarding the activity of known terrorist groups. Image credit: Johannes Zuurbier/FT
A Pentagon spokesman said that the Department of Defense (DoD) is taking the situation seriously.
"[The DoD] is aware of this issue and takes all unauthorized disclosures of controlled national security information or controlled unclassified information seriously," said Lt Cmdr Tim Gorman. "[Emails sent from .mil to .ml] are blocked before they leave the .mil domain, and the sender is notified that they must validate the email addresses of the intended recipients."
Gorman's statement is questionable since Zuurbier was still receiving mail intended for .mil domains as of last Wednesday. Either the DoD doesn't want to admit it has a problem to save face, it believes that acknowledgment will only attract more attention from bad actors, or it has fixed the situation within the last week.
Regardless of the DoD's stance, Zuurbier says more stray emails might be floating around in not-so-friendly hands. He related to FT that when he started managing Mali's email in 2013, he noticed many requests for domains like army.ml, navy.ml, etc. Such activity could indicate that hackers or other bad actors knew of the potential misaddressing and wanted to exploit it as they do with bogus domain names like wellfargo.com.
Following his lawyer's advice, Zuurbier began trying to inform someone in authority about the issue, which was nerve-wracking enough, considering he was handling a country's entire military email without authorization. He even gave his wife a copy of his lawyer's documents "just in case the black helicopters landed in [his] backyard."
Image credits: Guardsmen by Georgia National Guard, Email Snippets by Johannes Zuurbier/FT
https://www.techspot.com/news/99428-millions-us-military-emails-have-leaked-domain-russian.html