In brief: Those who value their digital privacy are always looking for new ways to block companies, hackers, or government agencies from spying on their online activities. If you're one of those individuals, Mozilla has some good news for you today: the organization has begun to rollout encrypted DNS over HTTPS (DoH) by default for US-based Firefox users.

The rollout will take place over the course of several weeks to ensure stability, but once it's finalized, all Firefox users running the latest version of the browser will have DNS protection. In short, DoH functionality helps to obfuscate and encrypt DNS lookup requests, which can otherwise expose information like the websites you visit.
Obviously, there's nothing inherently malicious about DNS lookups -- they're an essential part of the internet as we know it. Mozilla explains the technology as follows:
DNS is a database that links a human-friendly name, such as www.mozilla.org, to a computer-friendly series of numbers, called an IP address (e.g. 192.0.2.1). By performing a "lookup" in this database, your web browser is able to find websites on your behalf.
With DoH, third parties will have a much more difficult time harvesting your browsing data. "[DoH] helps hide your browsing history from attackers on the network, [and] helps prevent data collection by third parties on the network that ties your computer to websites you visit," Mozilla says.
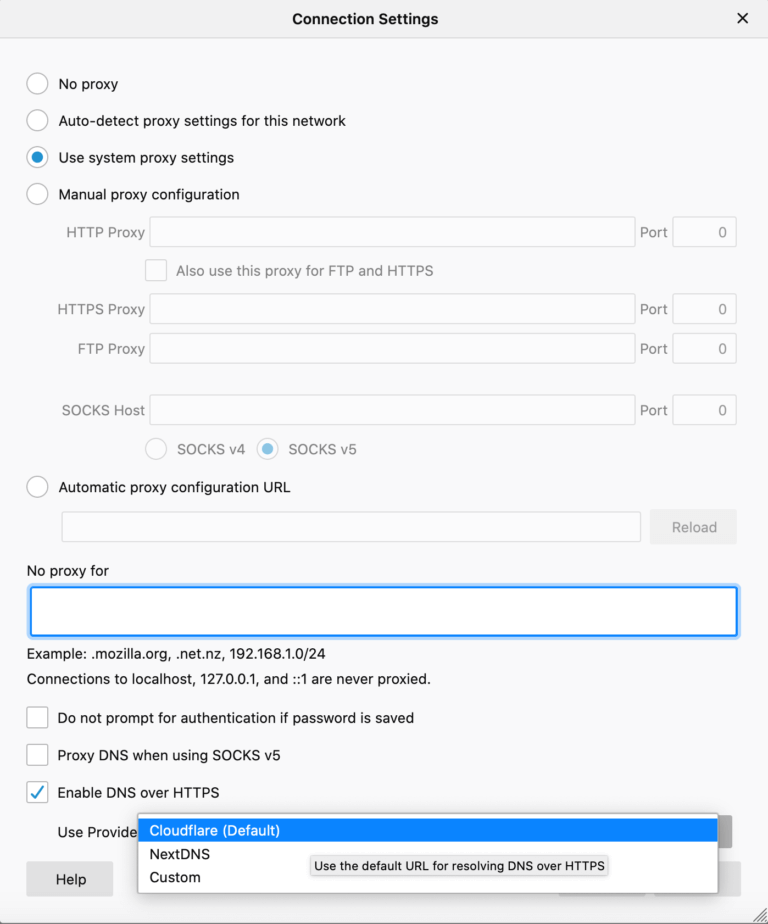
Right now, Mozilla's DoH implementation supports two "trusted resolvers" for encryption: Cloudflare and NextDNS. Other providers may get official support in the future, but for now, you'll have to rely on a custom alternative if you don't care for Cloudflare or NextDNS.
DoH will only be enabled by default for US-based Firefox users, but everybody can flip the switch manually if they so choose. Just visit Firefox's Options menu, go to General, scroll down to Network Settings, click the "Settings" button," and check the box for "Enable DNS over HTTPS." We're not sure why DoH isn't being turned on by default for non-US residents, but we'll be reaching out to Mozilla for clarification.
https://www.techspot.com/news/84157-mozilla-begins-rolling-out-dns-encryption-default-firefox.html