Just a few days after security researchers at Palo Alto Networks discovered the WireLurker malware that infects iOS devices through OS X, folks at mobile security research firm FireEye have uncovered an iOS security flaw that they claim poses a much bigger threat than WireLurker.
The vulnerability allows hackers to install fake third-party apps on an iOS device, replacing the original app with theirs, something which can be achieved by tricking users into installing the app by clicking a phishing link in a text message or email. FireEye has named the attack as “Masque Attack".
The attack takes advantage of a loophole in enterprise/ad-hoc provisioning, a system that lets enterprises deploy custom-built software without going through Apple's App Store, and allows apps coded with the same "bundle identifier" to be installed over each other.
To prove their claims, FireEye simulated the attack scenario through a malicious app named New Flappy Bird, which when installed was able to replace the original Gmail app on the phone.
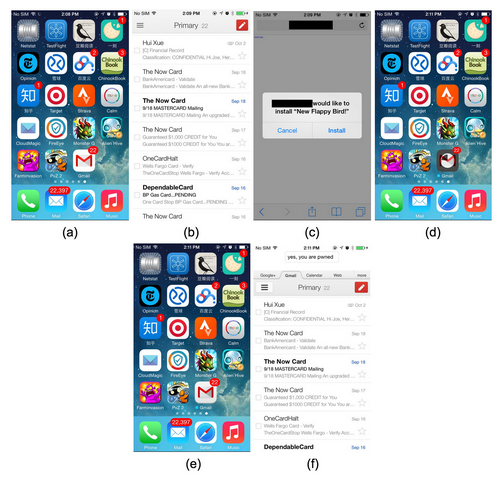
Figure (a) and (b) show the genuine Gmail app installed on the device with 22 unread emails. Figure (c) shows that the victim was lured to install an in-house app called New Flappy Bird from a website. After the victim clicks “Install”, Figure (d) shows the in-house app was replacing the original Gmail app during the installation. Figure (e) shows that the original Gmail app was replaced by the in-house app.
For differentiation purpose, the company placed the words yes, you are pwned at the top of the malicious Gmail app (Figure (f)).
FireEye says the attack, which can replace all apps except iOS preinstalled apps, works on iOS 7.1.1, 7.1.2, 8.0, 8.1, and 8.1.1 beta, for both jailbroken and non-jailbroken devices, and can be used to steal sensitive data.
The security firm claims they alerted Apple about this vulnerability back in July this year, but since it continues to exist, they decided to make it public so that iOS users know they are at risk.
Until the bug is fixed, users are advised to only download apps from Apple's official App Store.
https://www.techspot.com/news/58778-new-ios-bug-makes-devices-vulnerable-fake-app.html