Forward-looking: A team of researchers have devised a new method for protecting SSDs from ransomware attacks. It can detect ransomware, stop it in its tracks, and even recover stolen data in a matter of seconds. The cost should only be a minor increase in the SSD's latency.
The Register spoke with the researchers, who come from Inha University, the Daegu Gyeongbuk Institute of Science & Technology (DGIST), the University of Central Florida (UCF), and the Cyber Security Department at Ewha Womans University (EWU). The system, called SSD-Insider, is supposedly almost 100 percent accurate and has been tested on real-world ransomware.
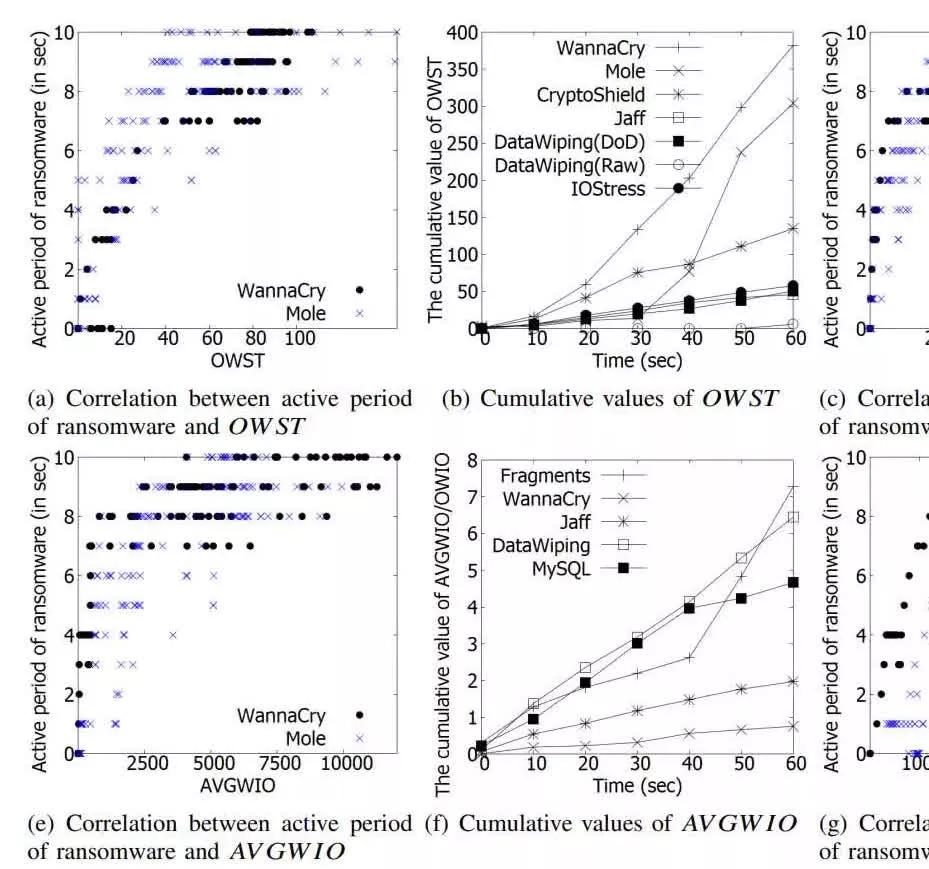
SSD-Insider works by recognizing certain patters in SSD activity that are known to indicate ransomware. "To recognize ransomware activity by viewing only the distribution of IO request headers, we have paid attention to a ransomware’s very unique behavior, overwriting," reads the team's research paper proposing SSD-Insider. It specifically points out the behavior of ransomware like WannaCry, Mole, and CryptoShield.
"When ransomware activity is detected by SSD-Insider++, input/output to the storage is suspended," Inha researcher DaeHun Nyang told The Register. "During the suspension, users can remove the ransomware process."
click to expand
After the ransomware is stopped, SSD-Insider can recover lost files due to the unique properties of SSDs. "SSDs always keep old versions of data that were overwritten by new data until they are permanently erased by [Garbage Collector]," the paper mentions. "SSD-Insider takes advantage of the built-in backup capability of SSDs. SSD-Insider keeps track of old versions of data inside SSDs and never removes them until the ransomware detection algorithm confirms that the new versions are not affected by ransomwares."
What's truly unique about SSD-Insider is that it works at the firmware level. The team designed SSD-Insider this way to help users who don't keep anti-ransomware software installed on their systems.
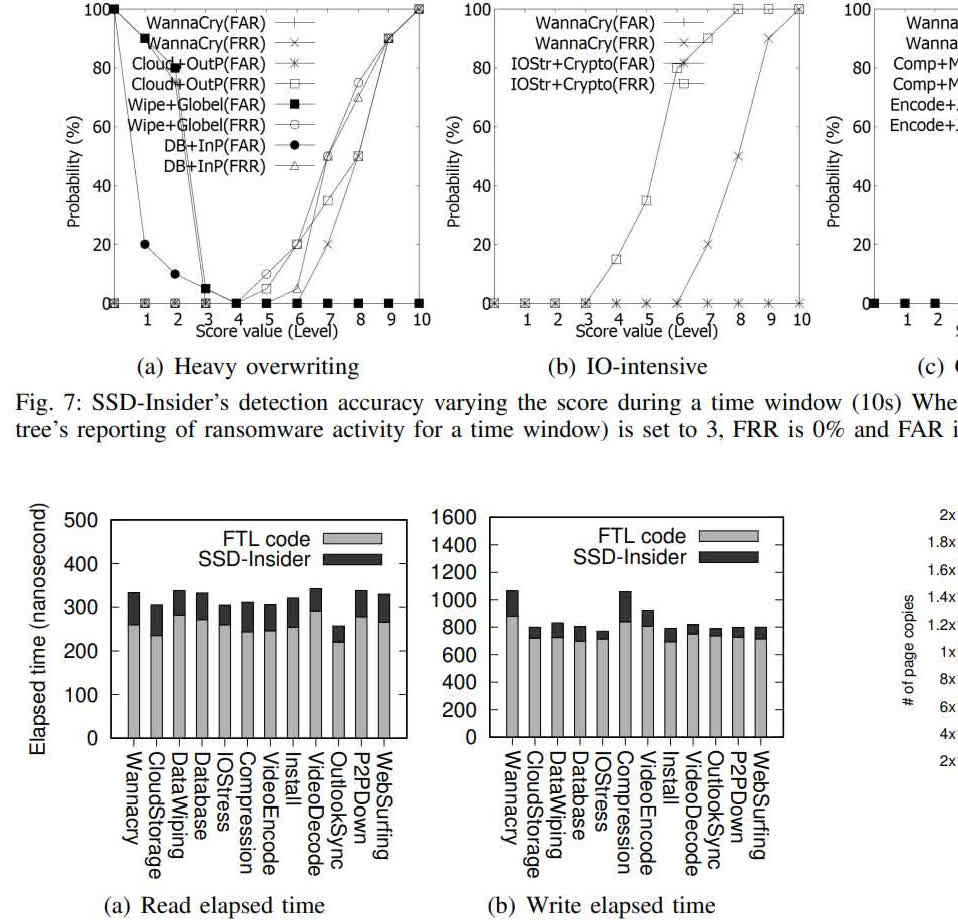
The paper also mentions the weaknesses of traditional software methods, like the ability of some ransomware to work against anti-virus software. SSD-Insider is also designed to have less CPU overhead than anti-ransomware software. The paper's abstract says SSD-Insider's software overhead is only around 147 to 254 nanoseconds.
click to expand
In testing with WannaCry and other ransomware, SSD-Insider never missed any ransomware activity, and rarely detected false positives. In all tested scenarios, the False Rejection Rate (FRR) was zero percent. The False Acceptance Rate (FAR) was nearly zero. "We report that the worst background noise in terms of FRR came from IO-intensive and CPU-intensive jobs" the researchers write. "In terms of FAR, the worst scenario came mostly from heavy overwriting type, such as DataWiping and Database applications."
An antivirus researcher told The Register a method like SSD-Insider isn't foolproof. "The function leverages a delay in deletion which means that ransomware developers would and could still bypass this feature with the knowledge of how this antidote operates," said ESET UK's Jake Moore. In any case, users should still keep their data backed up.