
We have all seen the message. You know, the one that says, “Your password is about to expire. Please create a new password.”
Then there are the subsequent messages that follow after we inevitably make an entry that the checker does not like: “Your password must be at least eight characters in length and contain at least one of each of the following: capital letter, lower case letter, number, and special character.” For me, it happens every three months on my office computer.
It’s annoying, but as an IT professional I have always accepted it as part and parcel of computer security. After all, the rules were published by the National Institute of Standards and Technology (NIST). Surely they knew what was best when creating strong and secure passwords, right?
As it turns out, they apparently didn’t know much more than the rest of us when the rules were written in 2003. The guidelines were published in a NIST document titled, “Special Publication 800-63. Appendix A.” Now the man who wrote them says he was mostly wrong.
Bill Burr, who worked as a midlevel manager at the NIST, authored the rules and recently told the Wall Street Journal, “Much of what I did I now regret.”
He had wanted to base his guidelines on real world data, but there just wasn't much available at the time. He even tried to get IT administrators at NIST to allow him to look at the passwords on the network, but they scoffed at him citing security concerns.
With nowhere else to turn Burr ended up relying heavily on a white paper written in the 1980s. The document was written well before the public had access to the internet. It was a time when cybercrime barely even existed, at least not as we know it today. Despite most of the advice in Special Publication 800-63 being off-base or outright wrong, the password rules within its pages became IT canon and remained so for almost 15 years.
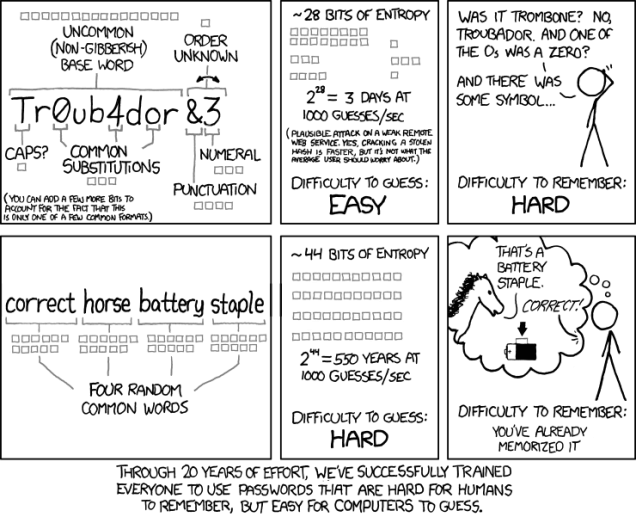
A widely shared comic strip (above) by Randall Munroe demonstrates the fallacy of Burr’s guidelines. It shows that a password using NIST’s rules can be cracked by a computer in 3 days, and is hard for us to remember. On the contrary, a simple passphrase of only four easy to remember words like "correct horse battery staple," would take 550 years to crack using the same brute force method.
“In the end, it was probably too complicated for a lot of folks to understand very well, and the truth is, it was barking up the wrong tree,” said the now retired 72-years-old Burr.
To that, the NIST has responded by rewriting the rules with today’s usage and users in mind. Paul Grassi headed up the re-write last June and said that many of the worst password commandments were eliminated. They initially thought it would be a quick edit, but they ended up starting over from scratch.
The new guidelines are only just beginning to trickle into the IT world, but some of the changes will have users and admins rejoicing.
“Drop the password-expiration advice and the requirement for special characters,” Grassi said. They did little for security and “actually had a negative impact on usability.”
Instead of a string of eight to 16 random characters, which never end up being random, we are told to use long, easy-to-remember phrases with the spaces removed (correcthorsebatterystaple). Grassi also says, “Users should be forced to change passwords only if there is a sign they may have been stolen.”
Sure, there are those that are going to hold on to the old guidelines because they hate change. Or those that like their password because they think "!'m@H4X0R" is cool. Or those that just don't care because they have a password manager that logs them in anyway. I'm just thankful that I can look forward to not having to get nagged to change my password every 90 days.
https://www.techspot.com/news/70492-man-who-came-up-password-rules-all-hate.html