The big picture: Late last year a security analyst with Tenable Research discovered a hardcoded backdoor in an access control system called PremiSys IDenticard. The software is used to create ID badges for employees and to remotely manage card readers to regulate access permission to various parts of a building.
According to James Sebree with Tenable Research, version 3.1.190 of PremiSys by IDenticard contains a backdoor that can allow an attacker access to administrative functions including adding, editing, and deletion of users in the badging system; assigning of permissions; and control over the readers within the building.
PremiSys is built on the .Net framework, so Sebree was able to reverse engineer the software by using Jetbrain's "dotPeek" .Net decompiler. When he discovered the vulnerability, he attempted contact with IDenticard to inform it of the problem multiple times. After 45 days with no response, Tenable notified CERT, which also attempted to contact the publisher. After 90 days, the firm had still not responded, so the discovery was publicly disclosed.
Disclosure Timeline
09/18/2018 - Initial Vulnerabilities Discovered.
10/05/2018 - Tenable attempts to contact Identicard via "Contact Us" email form.
10/22/2018 - Additional contact request e-mail sent to Identicard.
10/26/2018 - Tenable makes 3rd contact attempt to vendor (info@identicard.com).
11/06/2018 - Tenable makes 4th contact attempt to vendor (info@identicard.com).
11/19/2018 - Tenable contacts CERT.
11/19/2018 - Auto-response from CERT with VRF#18-11-NGYLM.
11/28/2018 - CERT assigns VU#822605 and inquires about contacting vendor.
11/29/2018 - CERT attempts to contact vendor via info@identicard.com on behalf of Tenable.
12/05/2018 - CERT reports that they have not heard back from the vendor.
12/11/2018 - Tenable attempts final contact with vendor informing them of public disclosure date.
01/04/2019 - Tenable informs CERT of upcoming advisory publication.
01/08/2019 - Tenable publicly discloses vulnerabilities.
Tenable did not have access to the physical components of the system, so it had to take an overview of the hosting service aspect of the program.
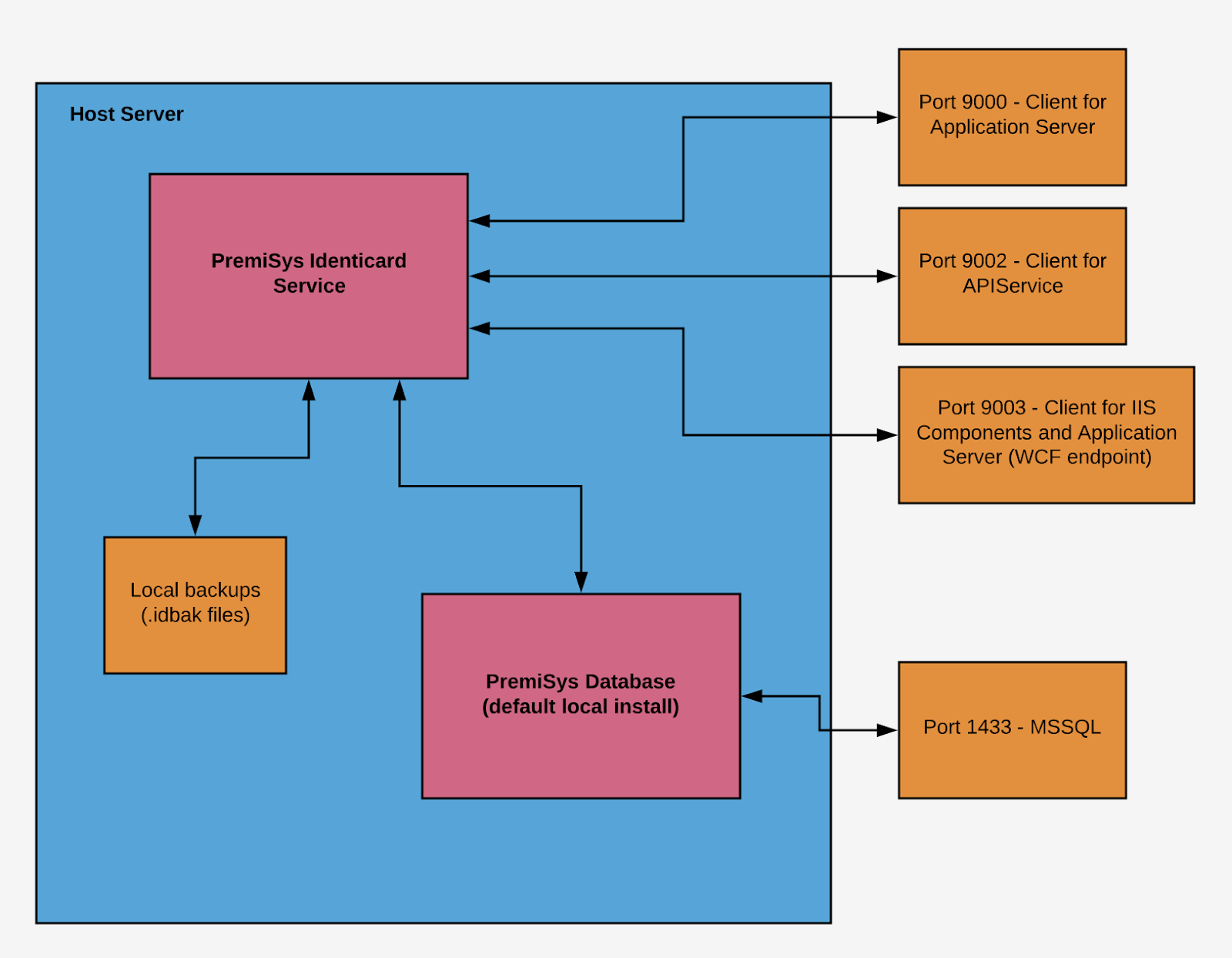
"Creating a reasonable threat model for the entire badge system, badge printers, authentication mechanisms, locks, badges, etc. would have been impractical for the limited amount of time I had," said Sebree. "Fortunately, since I didn't have access to most of these components in the first place, simply targeting and mapping the attack surface of the hosting service was much simpler."
The authentication routine within PremiSys contains a function called IgnoreAuthentication(). This command does exactly what it says as long at the hardcoded credentials are being used.
The scope of the vulnerability is rather broad as IDenticard's software is widely used. The company's website touts it as being used by Fortune 500 companies, K-12 schools, colleges and universities, medical centers, factories, and local, state and federal government agencies and offices.
Tenable Research says that there is no solution to this problem at this time. Since it is a hardcoded vulnerability, it is going to have to be patched by IDenticard. So far the company has not responded to the disclosure.
