Why it matters: In a world where cyberattacks can devastate critical infrastructure, governments, law enforcement, and public institutions use so-called "air-gapped" systems to prevent even the most ambitious attempts. That said, a team of Israeli security researchers still manages to regularly come up with ideas on how organizations may be able to improve their security posture.
For years, Israeli security researchers at Ben Gurion University have been busy looking for ways malicious actors can exploit physically isolated computers to exfiltrate sensitive data. The team headed by Dr. Mordechai Guri is well-known for finding novel and unorthodox methods of accessing so-called air-gapped systems.
Various techniques they have discovered include using computer RAM as a small Wi-Fi transmitter, manipulating display brightness to send ones and zeroes through security cameras, or tuning the speed of cooling fans to create vibrations that can be easily recorded using a smartphone.
The researchers have recently developed a pair of attack methods dubbed Gairoscope and EtherLED. As explained in the two associated research papers, these new exploits are a reminder that inventive hackers can work around even the strictest security measures using relatively simple principles.

As the name suggests, the Gairoscope attack relies on a smartphone gyroscope, a microelectromechanical (MEMS) device susceptible to mechanical oscillations. In this case, the researchers use a specially-crafted piece of malware that can output "covert acoustic sound waves" using computer speakers.
A smartphone gyroscope easily picks up these air vibrations but does require additional work. The researchers explain that many mobile apps use gyroscopes to enhance the user experience. So users are more likely to approve app access to the gyroscope than the microphone --- a behavior that attackers can exploit.
Another benefit of this method is that there's no visual indicator on iOS or Android for when the gyroscope is in use, while there is one that gives the user a heads-up when the microphone is active. This opens new avenues for the smartphone side of the exploit, such as injecting the malicious JavaScript code on a legitimate website or web app instead of jumping through hoops to run malware on the device.
The Gairoscope method allows an attacker to exfiltrate data at up to eight bits per second, faster than most known covert acoustic methods. It may not seem like much, but it should be enough to transmit valuable information such as passwords, storage encryption keys, and more.
Guri and his team were able to use an Android app to decode a message typed on the target computer in a few seconds (video above). However, a significant limitation is that the maximum distance for reliable transmission is eight meters (26 feet).
Securing against Gairoscope can be done by either prohibiting speaker use or filtering out resonance frequencies generated by air-gapped systems using a special audio filter.
The second attack method relies on the green and amber status and activity indicator LEDs found on many network adapters. Previously, Guri's team had devised exploits based on activity lights found on hard disk drives, switches, Wi-Fi routers, and keyboards, with data transmission speeds of up to 6,000 bits per second.
EtherLED is a bit more tricky to pull off, as it requires a direct line of sight between the target device and any surveillance cameras the attacker might be able to compromise. It would also be possible for someone to use a drone to exfiltrate the sensitive data, provided the network activity lights face a window.
Using security cameras is a lot more feasible, however. Last year, hackers accessed 150,000 cameras inside schools, hospitals, police stations, prisons, and companies like Tesla and Equinox. From there, all they'd have to do is record the blinking lights of an infected network interface card to steal data.
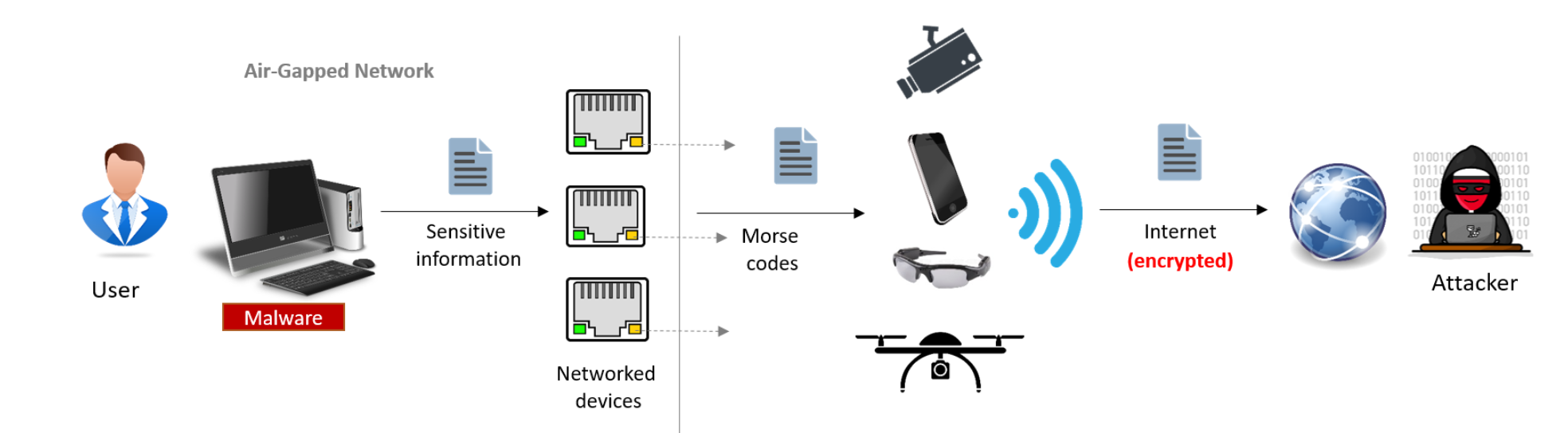
In the associated paper, Guri explains EtherLED can be used to leak a password in one second and an RSA key in a little less than a minute. The speed varies depending on the modulation used and whether the attackers could compromise the driver or the network card's firmware. The maximum distance for reliable data transmission ranges from 10 to 100 meters, depending on the camera.
Mitigating against the attack can be done in several ways, ranging from covering the LEDs with black tape to deploying firmware-level countermeasures that scramble any visual signals the attackers may try to use.
As easy as it is to dismiss the possibility of attacks like Gairoscope and EtherLED occurring in the wild, this research is still essential. Over the past two years, we've seen reports detailing cyber espionage groups targeting air-gapped systems in South Korea and Japan.
Masthead credit: FLYD
