A hot potato: Threat actors are including OneNote attachments in their phishing emails to infect victims with remote access malware that can be used to steal passwords or even access cryptocurrency wallets. Malicious Word and Excel attachments that launch macros to download and install malware have been used by attackers to distribute malware through emails for years. However, Microsoft finally disabled macros by default in Office documents in 2022, rendering this technique of virus distribution ineffective.
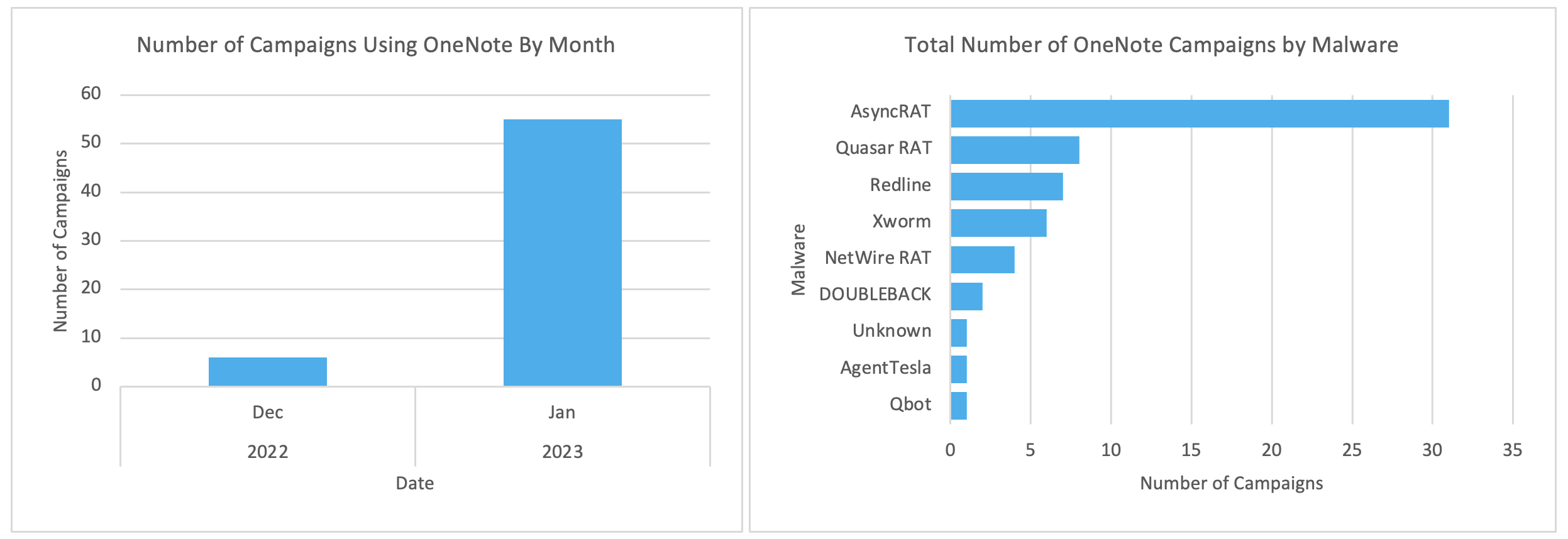
The use of Microsoft OneNote pages to disseminate malware to unwary users is increasing according to security experts. The researchers at Proofpoint claim they found six campaigns in December 2022 that used OneNote to distribute the AsyncRAT malware in a thorough study. Less than a month later, they detected over 50 campaigns in January 2023. The same month, a threat actor called TA577 started distributing Qbot via OneNote
XWorm, Qakbot, BATLOADER, Agent Tesla, DOUBLEBACK, Quasar RAT, AsyncRAT, RedLine Stealer, and FormBook are a few well-known malware families that use this method of dissemination.
OneNote files allow users to insert attachments, which have the potential to download malware from remote locations. The report says that hackers were passing out Notebooks with messages such as "invoice, remittance, shipment, and seasonal themes like Christmas bonus," deceiving their targets into thinking the content was secure.
Occasionally, the email phishing enticements contain a OneNote file, which embeds an HTA file that launches a PowerShell script to retrieve a malicious payload from a remote server. In other scenarios, a malicious VBScript embedded in the OneNote page and concealed by an image that appears to be a useful button is executed. The VBScript, on the other hand, is designed to execute the Doubleback PowerShell script.
Even though email remains the most common method for spreading malware, restricting macros has the dual effect of reducing the attack surface and raising the overhead associated with conducting an attack. But other strategies have also gained popularity hiding a malicious code. The Ekipa RAT (remote access trojan) and other backdoors have also been distributed via Microsoft Publisher macros and Excel add-in (XLL) files as attack vectors.
Researchers at Proofpoint think that OneNote's popularity among hackers is the outcome of an in-depth investigation. OneNote, which is part of the Microsoft Office suite but also now offered for free as a standalone program, was chosen after some trial and error with several attachment types because the detection rates have been low thus far.