While Macs don't get hit by malware as often as Windows, it still happens now and then. When it does, it can be just as threatening. The Fruitfly malware discovered earlier this year is a perfect example, and security researchers are saying that it is still a threat despite Apple having issued a patch.
The malware, dubbed Fruitfly by Apple but detected as OSX.Backdoor.Quimitchin by Malwarebytes, is a nasty backdoor into OS X discovered back in January. Malwarebytes was alerted to it by a system admin who discovered it when he noticed unusual outgoing network traffic. Researchers studying the malicious software found that it had mostly been aimed at biomedical research centers.
Malwarebytes informed Apple of the security threat and a patch was pushed out to protect against it. However, ZDNet reports that six months later, Macs are still turning up infected. Synack's Chief Security Researcher Patrick Wardle, says that the malware is not as widespread, but it's still out there despite the patch. The malware is feature complete and capable of taking over the computer entirely.
"[An operator] could take complete control of an infected Mac, including its keyboard and mouse, take screenshots of the display, remotely switch on the webcam, and modify files. The malware can also run commands in the background, and even kill the malware's process altogether – likely in an effort to avoid detection."
Wardle created a command and control (C&C) server that could connect and communicate with a sample of Fruitfly in his lab. He discovered that not only could he take over the infected computer, but the software also alerted him if the victim was active, a sort of stealth warning system. It also had a kill switch that could end the application's process to avoid detection.
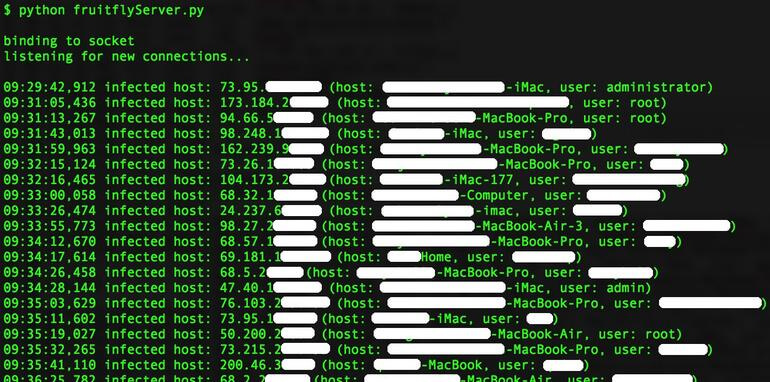
He tested his C&C scripts with online servers and was shocked when he began getting information on numerous infected computers connecting to the servers. "I thought – 'f**k!' – I have to be responsible here," he said. Aside from the C&C capabilities, he was able to see each user's IP address, user name, and computer name, which he said was typically the full name of the user.
Ninety percent of the users that connected to the C&C servers were located in the US, and most were individual users rather than groups such as companies or research firms as the early reports had indicated. Wardle believes that the malware is not state-controlled, but rather is operated by a single hacker to spy on people for "perverse reasons."
The delivery method for the malware could probably come through a malicious email attachment. It goes without saying, never open an email that you aren't expecting.