DragonMaster Jay,
Thanks for all you are doing. Here are the three reports.
----------------------------------------------------
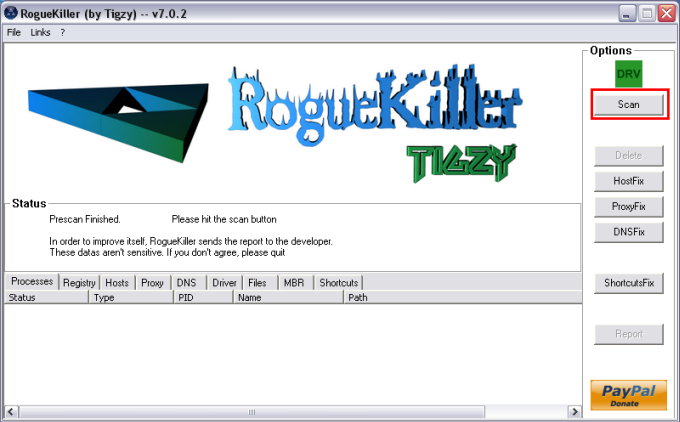
RogueKiller V8.0.2 [08/31/2012] by Tigzy
mail: tigzyRK<at>gmail<dot>com
Feedback:
https://www.techspot.com/downloads/5562-roguekiller.html
Blog:
http://tigzyrk.blogspot.com
Operating System: Windows 7 (6.1.7601 Service Pack 1) 32 bits version
Started in : Normal mode
User : Michael [Admin rights]
Mode : Scan -- Date : 09/13/2012 08:08:15
¤¤¤ Bad processes : 4 ¤¤¤
[SUSP PATH][DLL] explorer.exe -- C:\Windows\explorer.exe : C:\ProgramData\Ad-Aware Browsing Protection\adawarebp.dll -> UNLOADED
[SUSP PATH] NUA.exe -- C:\ProgramData\Norton\NUA.exe -> KILLED [TermProc]
[SUSP PATH][DLL] rundll32.exe -- C:\Windows\System32\rundll32.exe : -> KILLED [TermProc]
[SUSP PATH][DLL] rundll32.exe -- C:\Windows\System32\rundll32.exe : -> KILLED [TermProc]
¤¤¤ Registry Entries : 9 ¤¤¤
[RUN][SUSP PATH] HKCU\[...]\Run : NortonUpdateAgent (C:\ProgramData\Norton\NUA.exe) -> FOUND
[RUN][SUSP PATH] HKUS\S-1-5-21-3716613784-1258854080-1605684737-1000[...]\Run : NortonUpdateAgent (C:\ProgramData\Norton\NUA.exe) -> FOUND
[TASK][RESIDU] ProgramDataUpdater : C:\Windows\System32\rundll32.exe -> FOUND
[TASK][RESIDU] Proxy : C:\Windows\System32\rundll32.exe -> FOUND
[TASK][RESIDU] SR : C:\Windows\System32\rundll32.exe -> FOUND
[TASK][RESIDU] IpAddressConflict1 : C:\Windows\System32\rundll32.exe -> FOUND
[TASK][RESIDU] IpAddressConflict2 : C:\Windows\System32\rundll32.exe -> FOUND
[HJ] HKLM\[...]\System : ConsentPromptBehaviorAdmin (0) -> FOUND
[HJ] HKLM\[...]\System : EnableLUA (0) -> FOUND
¤¤¤ Particular Files / Folders: ¤¤¤
¤¤¤ Driver : [LOADED] ¤¤¤
SSDT[13] : NtAlertResumeThread @ 0x832FCCA9 -> HOOKED (Unknown @ 0x86D4DB18)
SSDT[14] : NtAlertThread @ 0x8324FBC0 -> HOOKED (Unknown @ 0x86D4C388)
SSDT[19] : NtAllocateVirtualMemory @ 0x83248BCC -> HOOKED (Unknown @ 0x86FE07E8)
SSDT[22] : NtAlpcConnectPort @ 0x8329444E -> HOOKED (Unknown @ 0x865170B8)
SSDT[43] : NtAssignProcessToJobObject @ 0x8321DFCA -> HOOKED (Unknown @ 0x86D79128)
SSDT[74] : NtCreateMutant @ 0x8322F28E -> HOOKED (Unknown @ 0x86FE7720)
SSDT[86] : NtCreateSymbolicLinkObject @ 0x832208ED -> HOOKED (Unknown @ 0x86477E98)
SSDT[87] : NtCreateThread @ 0x832FAED6 -> HOOKED (Unknown @ 0x86FE67F0)
SSDT[88] : NtCreateThreadEx @ 0x8328F34B -> HOOKED (Unknown @ 0x86477F68)
SSDT[96] : NtDebugActiveProcess @ 0x832CCDB0 -> HOOKED (Unknown @ 0x86D73A90)
SSDT[111] : NtDuplicateObject @ 0x8325065A -> HOOKED (Unknown @ 0x86FE0940)
SSDT[131] : NtFreeVirtualMemory @ 0x830D847A -> HOOKED (Unknown @ 0x86FE7E68)
SSDT[145] : NtImpersonateAnonymousToken @ 0x832148BC -> HOOKED (Unknown @ 0x86D61350)
SSDT[147] : NtImpersonateThread @ 0x8329884C -> HOOKED (Unknown @ 0x86D612D8)
SSDT[155] : NtLoadDriver @ 0x831E4BFC -> HOOKED (Unknown @ 0x8629DA98)
SSDT[168] : NtMapViewOfSection @ 0x83265512 -> HOOKED (Unknown @ 0x86FE7D88)
SSDT[177] : NtOpenEvent @ 0x8322EC8A -> HOOKED (Unknown @ 0x86D6A628)
SSDT[190] : NtOpenProcess @ 0x83230AD4 -> HOOKED (Unknown @ 0x86FE0AE0)
SSDT[191] : NtOpenProcessToken @ 0x8328321F -> HOOKED (Unknown @ 0x86CEC948)
SSDT[194] : NtOpenSection @ 0x8328889B -> HOOKED (Unknown @ 0x86D6E130)
SSDT[198] : NtOpenThread @ 0x8327CF95 -> HOOKED (Unknown @ 0x86FE0A10)
SSDT[215] : NtProtectVirtualMemory @ 0x83261581 -> HOOKED (Unknown @ 0x86FE7058)
SSDT[304] : NtResumeThread @ 0x8328F572 -> HOOKED (Unknown @ 0x86D3C920)
SSDT[316] : NtSetContextThread @ 0x832FC755 -> HOOKED (Unknown @ 0x86D2E118)
SSDT[333] : NtSetInformationProcess @ 0x8325776D -> HOOKED (Unknown @ 0x86FE7C30)
SSDT[350] : NtSetSystemInformation @ 0x8326D26C -> HOOKED (Unknown @ 0x86D73048)
SSDT[366] : NtSuspendProcess @ 0x832FCBE3 -> HOOKED (Unknown @ 0x86D6FF90)
SSDT[367] : NtSuspendThread @ 0x832B4085 -> HOOKED (Unknown @ 0x86D3C068)
SSDT[370] : NtTerminateProcess @ 0x83279BCD -> HOOKED (Unknown @ 0x86CEA4C8)
SSDT[371] : NtTerminateThread @ 0x83297584 -> HOOKED (Unknown @ 0x86D32B90)
SSDT[385] : NtUnmapViewOfSection @ 0x8328385A -> HOOKED (Unknown @ 0x86D25760)
SSDT[399] : NtWriteVirtualMemory @ 0x8327E92A -> HOOKED (Unknown @ 0x86FE7F38)
S_SSDT[318] : Unknown -> HOOKED (Unknown @ 0x87E1D2E8)
S_SSDT[402] : Unknown -> HOOKED (Unknown @ 0x87E0E2C8)
S_SSDT[434] : Unknown -> HOOKED (Unknown @ 0x87E02390)
S_SSDT[436] : Unknown -> HOOKED (Unknown @ 0x87E26E00)
S_SSDT[448] : Unknown -> HOOKED (Unknown @ 0x87BCC210)
S_SSDT[490] : Unknown -> HOOKED (Unknown @ 0x87E41E08)
S_SSDT[508] : Unknown -> HOOKED (Unknown @ 0x87E1A7A8)
S_SSDT[509] : Unknown -> HOOKED (Unknown @ 0x87E29E08)
S_SSDT[585] : Unknown -> HOOKED (Unknown @ 0x87BD90B0)
S_SSDT[588] : Unknown -> HOOKED (Unknown @ 0x87E111D8)
IRP[IRP_MJ_CREATE] : \SystemRoot\system32\drivers\atapi.sys -> HOOKED ([MAJOR] Unknown @ 0x850B71F8)
IRP[IRP_MJ_CLOSE] : \SystemRoot\system32\drivers\atapi.sys -> HOOKED ([MAJOR] Unknown @ 0x850B71F8)
IRP[IRP_MJ_DEVICE_CONTROL] : \SystemRoot\system32\drivers\atapi.sys -> HOOKED ([MAJOR] Unknown @ 0x850B71F8)
IRP[IRP_MJ_INTERNAL_DEVICE_CONTROL] : \SystemRoot\system32\drivers\atapi.sys -> HOOKED ([MAJOR] Unknown @ 0x850B71F8)
IRP[IRP_MJ_POWER] : \SystemRoot\system32\drivers\atapi.sys -> HOOKED ([MAJOR] Unknown @ 0x850B71F8)
IRP[IRP_MJ_SYSTEM_CONTROL] : \SystemRoot\system32\drivers\atapi.sys -> HOOKED ([MAJOR] Unknown @ 0x850B71F8)
IRP[IRP_MJ_PNP] : \SystemRoot\system32\drivers\atapi.sys -> HOOKED ([MAJOR] Unknown @ 0x850B71F8)
¤¤¤ Infection : ¤¤¤
¤¤¤ HOSTS File: ¤¤¤
--> C:\windows\system32\drivers\etc\hosts
127.0.0.1 localhost
¤¤¤ MBR Check: ¤¤¤
+++++ PhysicalDrive0: +++++
--- User ---
[MBR] 5f9074452f51f11d2d580847a94ef254
[BSP] 8e7f089651944c89a69681dea7db699e : Windows 7 MBR Code
Partition table:
0 - [ACTIVE] NTFS (0x07) [VISIBLE] Offset (sectors): 2048 | Size: 102400 Mo
1 - [XXXXXX] NTFS (0x07) [VISIBLE] Offset (sectors): 209717248 | Size: 125816 Mo
2 - [XXXXXX] FAT32 (0x1b) [HIDDEN!] Offset (sectors): 467388416 | Size: 10240 Mo
3 - [XXXXXX] UNKNOWN (0xef) [VISIBLE] Offset (sectors): 488359936 | Size: 15 Mo
User = LL1 ... OK!
User = LL2 ... OK!
Finished : << RKreport[1].txt >>
RKreport[1].txt
RogueKiller V8.0.2 [08/31/2012] by Tigzy
mail: tigzyRK<at>gmail<dot>com
Feedback:
https://www.techspot.com/downloads/5562-roguekiller.html
Blog:
http://tigzyrk.blogspot.com
Operating System: Windows 7 (6.1.7601 Service Pack 1) 32 bits version
Started in : Normal mode
User : Michael [Admin rights]
Mode : Remove -- Date : 09/13/2012 08:10:25
¤¤¤ Bad processes : 4 ¤¤¤
[SUSP PATH][DLL] explorer.exe -- C:\Windows\explorer.exe : C:\ProgramData\Ad-Aware Browsing Protection\adawarebp.dll -> UNLOADED
[SUSP PATH] NUA.exe -- C:\ProgramData\Norton\NUA.exe -> KILLED [TermProc]
[SUSP PATH][DLL] rundll32.exe -- C:\Windows\System32\rundll32.exe : -> KILLED [TermProc]
[SUSP PATH][DLL] rundll32.exe -- C:\Windows\System32\rundll32.exe : -> KILLED [TermProc]
¤¤¤ Registry Entries : 8 ¤¤¤
[RUN][SUSP PATH] HKCU\[...]\Run : NortonUpdateAgent (C:\ProgramData\Norton\NUA.exe) -> DELETED
[TASK][RESIDU] ProgramDataUpdater : C:\Windows\System32\rundll32.exe -> DELETED
[TASK][RESIDU] Proxy : C:\Windows\System32\rundll32.exe -> DELETED
[TASK][RESIDU] SR : C:\Windows\System32\rundll32.exe -> DELETED
[TASK][RESIDU] IpAddressConflict1 : C:\Windows\System32\rundll32.exe -> DELETED
[TASK][RESIDU] IpAddressConflict2 : C:\Windows\System32\rundll32.exe -> DELETED
[HJ] HKLM\[...]\System : ConsentPromptBehaviorAdmin (0) -> REPLACED (2)
[HJ] HKLM\[...]\System : EnableLUA (0) -> REPLACED (1)
¤¤¤ Particular Files / Folders: ¤¤¤
¤¤¤ Driver : [LOADED] ¤¤¤
SSDT[13] : NtAlertResumeThread @ 0x832FCCA9 -> HOOKED (Unknown @ 0x86D4DB18)
SSDT[14] : NtAlertThread @ 0x8324FBC0 -> HOOKED (Unknown @ 0x86D4C388)
SSDT[19] : NtAllocateVirtualMemory @ 0x83248BCC -> HOOKED (Unknown @ 0x86FE07E8)
SSDT[22] : NtAlpcConnectPort @ 0x8329444E -> HOOKED (Unknown @ 0x865170B8)
SSDT[43] : NtAssignProcessToJobObject @ 0x8321DFCA -> HOOKED (Unknown @ 0x86D79128)
SSDT[74] : NtCreateMutant @ 0x8322F28E -> HOOKED (Unknown @ 0x86FE7720)
SSDT[86] : NtCreateSymbolicLinkObject @ 0x832208ED -> HOOKED (Unknown @ 0x86477E98)
SSDT[87] : NtCreateThread @ 0x832FAED6 -> HOOKED (Unknown @ 0x86FE67F0)
SSDT[88] : NtCreateThreadEx @ 0x8328F34B -> HOOKED (Unknown @ 0x86477F68)
SSDT[96] : NtDebugActiveProcess @ 0x832CCDB0 -> HOOKED (Unknown @ 0x86D73A90)
SSDT[111] : NtDuplicateObject @ 0x8325065A -> HOOKED (Unknown @ 0x86FE0940)
SSDT[131] : NtFreeVirtualMemory @ 0x830D847A -> HOOKED (Unknown @ 0x86FE7E68)
SSDT[145] : NtImpersonateAnonymousToken @ 0x832148BC -> HOOKED (Unknown @ 0x86D61350)
SSDT[147] : NtImpersonateThread @ 0x8329884C -> HOOKED (Unknown @ 0x86D612D8)
SSDT[155] : NtLoadDriver @ 0x831E4BFC -> HOOKED (Unknown @ 0x8629DA98)
SSDT[168] : NtMapViewOfSection @ 0x83265512 -> HOOKED (Unknown @ 0x86FE7D88)
SSDT[177] : NtOpenEvent @ 0x8322EC8A -> HOOKED (Unknown @ 0x86D6A628)
SSDT[190] : NtOpenProcess @ 0x83230AD4 -> HOOKED (Unknown @ 0x86FE0AE0)
SSDT[191] : NtOpenProcessToken @ 0x8328321F -> HOOKED (Unknown @ 0x86CEC948)
SSDT[194] : NtOpenSection @ 0x8328889B -> HOOKED (Unknown @ 0x86D6E130)
SSDT[198] : NtOpenThread @ 0x8327CF95 -> HOOKED (Unknown @ 0x86FE0A10)
SSDT[215] : NtProtectVirtualMemory @ 0x83261581 -> HOOKED (Unknown @ 0x86FE7058)
SSDT[304] : NtResumeThread @ 0x8328F572 -> HOOKED (Unknown @ 0x86D3C920)
SSDT[316] : NtSetContextThread @ 0x832FC755 -> HOOKED (Unknown @ 0x86D2E118)
SSDT[333] : NtSetInformationProcess @ 0x8325776D -> HOOKED (Unknown @ 0x86FE7C30)
SSDT[350] : NtSetSystemInformation @ 0x8326D26C -> HOOKED (Unknown @ 0x86D73048)
SSDT[366] : NtSuspendProcess @ 0x832FCBE3 -> HOOKED (Unknown @ 0x86D6FF90)
SSDT[367] : NtSuspendThread @ 0x832B4085 -> HOOKED (Unknown @ 0x86D3C068)
SSDT[370] : NtTerminateProcess @ 0x83279BCD -> HOOKED (Unknown @ 0x86CEA4C8)
SSDT[371] : NtTerminateThread @ 0x83297584 -> HOOKED (Unknown @ 0x86D32B90)
SSDT[385] : NtUnmapViewOfSection @ 0x8328385A -> HOOKED (Unknown @ 0x86D25760)
SSDT[399] : NtWriteVirtualMemory @ 0x8327E92A -> HOOKED (Unknown @ 0x86FE7F38)
S_SSDT[318] : Unknown -> HOOKED (Unknown @ 0x87E1D2E8)
S_SSDT[402] : Unknown -> HOOKED (Unknown @ 0x87E0E2C8)
S_SSDT[434] : Unknown -> HOOKED (Unknown @ 0x87E02390)
S_SSDT[436] : Unknown -> HOOKED (Unknown @ 0x87E26E00)
S_SSDT[448] : Unknown -> HOOKED (Unknown @ 0x87BCC210)
S_SSDT[490] : Unknown -> HOOKED (Unknown @ 0x87E41E08)
S_SSDT[508] : Unknown -> HOOKED (Unknown @ 0x87E1A7A8)
S_SSDT[509] : Unknown -> HOOKED (Unknown @ 0x87E29E08)
S_SSDT[585] : Unknown -> HOOKED (Unknown @ 0x87BD90B0)
S_SSDT[588] : Unknown -> HOOKED (Unknown @ 0x87E111D8)
IRP[IRP_MJ_CREATE] : \SystemRoot\system32\drivers\atapi.sys -> HOOKED ([MAJOR] Unknown @ 0x850B71F8)
IRP[IRP_MJ_CLOSE] : \SystemRoot\system32\drivers\atapi.sys -> HOOKED ([MAJOR] Unknown @ 0x850B71F8)
IRP[IRP_MJ_DEVICE_CONTROL] : \SystemRoot\system32\drivers\atapi.sys -> HOOKED ([MAJOR] Unknown @ 0x850B71F8)
IRP[IRP_MJ_INTERNAL_DEVICE_CONTROL] : \SystemRoot\system32\drivers\atapi.sys -> HOOKED ([MAJOR] Unknown @ 0x850B71F8)
IRP[IRP_MJ_POWER] : \SystemRoot\system32\drivers\atapi.sys -> HOOKED ([MAJOR] Unknown @ 0x850B71F8)
IRP[IRP_MJ_SYSTEM_CONTROL] : \SystemRoot\system32\drivers\atapi.sys -> HOOKED ([MAJOR] Unknown @ 0x850B71F8)
IRP[IRP_MJ_PNP] : \SystemRoot\system32\drivers\atapi.sys -> HOOKED ([MAJOR] Unknown @ 0x850B71F8)
¤¤¤ Infection : ¤¤¤
¤¤¤ HOSTS File: ¤¤¤
--> C:\windows\system32\drivers\etc\hosts
127.0.0.1 localhost
¤¤¤ MBR Check: ¤¤¤
+++++ PhysicalDrive0: +++++
--- User ---
[MBR] 5f9074452f51f11d2d580847a94ef254
[BSP] 8e7f089651944c89a69681dea7db699e : Windows 7 MBR Code
Partition table:
0 - [ACTIVE] NTFS (0x07) [VISIBLE] Offset (sectors): 2048 | Size: 102400 Mo
1 - [XXXXXX] NTFS (0x07) [VISIBLE] Offset (sectors): 209717248 | Size: 125816 Mo
2 - [XXXXXX] FAT32 (0x1b) [HIDDEN!] Offset (sectors): 467388416 | Size: 10240 Mo
3 - [XXXXXX] UNKNOWN (0xef) [VISIBLE] Offset (sectors): 488359936 | Size: 15 Mo
User = LL1 ... OK!
User = LL2 ... OK!
Finished : << RKreport[2].txt >>
RKreport[1].txt ; RKreport[2].txt
RogueKiller V8.0.2 [08/31/2012] by Tigzy
mail: tigzyRK<at>gmail<dot>com
Feedback:
https://www.techspot.com/downloads/5562-roguekiller.html
Blog:
http://tigzyrk.blogspot.com
Operating System: Windows 7 (6.1.7601 Service Pack 1) 32 bits version
Started in : Normal mode
User : Michael [Admin rights]
Mode : Shortcuts HJfix -- Date : 09/13/2012 08:12:36
¤¤¤ Bad processes : 4 ¤¤¤
[SUSP PATH][DLL] explorer.exe -- C:\Windows\explorer.exe : C:\ProgramData\Ad-Aware Browsing Protection\adawarebp.dll -> UNLOADED
[SUSP PATH] NUA.exe -- C:\ProgramData\Norton\NUA.exe -> KILLED [TermProc]
[SUSP PATH][DLL] rundll32.exe -- C:\Windows\System32\rundll32.exe : -> KILLED [TermProc]
[SUSP PATH][DLL] rundll32.exe -- C:\Windows\System32\rundll32.exe : -> KILLED [TermProc]
¤¤¤ Driver : [LOADED] ¤¤¤
¤¤¤ File attributes restored: ¤¤¤
Desktop: Success 0 / Fail 0
Quick launch: Success 0 / Fail 0
Programs: Success 1 / Fail 0
Start menu: Success 0 / Fail 0
User folder: Success 27 / Fail 0
My documents: Success 0 / Fail 0
My favorites: Success 0 / Fail 0
My pictures: Success 0 / Fail 0
My music: Success 0 / Fail 0
My videos: Success 0 / Fail 0
Local drives: Success 26 / Fail 6
Backup: [NOT FOUND]
Drives:
[C:] \Device\HarddiskVolume1 -- 0x3 --> Restored
[D:] \Device\HarddiskVolume2 -- 0x3 --> Restored
[E:] \Device\CdRom0 -- 0x5 --> Skipped
[F:] \Device\HarddiskVolume5 -- 0x2 --> Restored
¤¤¤ Infection : ¤¤¤
Finished : << RKreport[3].txt >>
RKreport[1].txt ; RKreport[2].txt ; RKreport[3].txt
Michael