Not all hacks are malicious. Much like the attack on child porn-hosting Dark Web service FH2, some are carried out with good intentions. This appears to be the case with white-hat security enthusiast Stackoverflowin, who recently commandeered 150,000 printers left accessible via the internet.
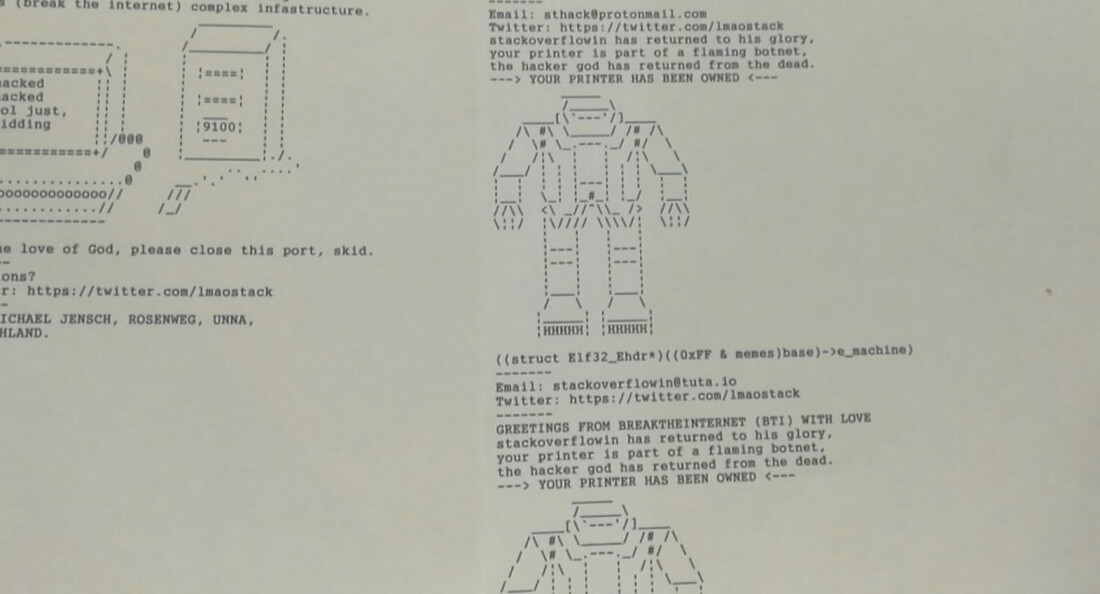
Over the weekend, printers from large offices, homes, and even the tiny receipt printers in restaurants across the world suddenly started printing out various messages, including: “stackoverflowin the hacker god has returned, your printer is part of a flaming botnet, operating on putin’s forehead utilising BTI’s (break the Internet) complete infrastructure,” and “for the love of God, please close this port, skid [script kiddie].” They included some ASCII art of robots and a computer, along with Stackoverflowin’s email address and twitter handle.
I'm honestly just impressed with these printer hacks more than anything. Thanks for entertaining me during my double shift @lmaostack pic.twitter.com/EzFXmqmDeo
— Faith Kennedy (@faithers99) February 4, 2017
The hacker achieved this by writing and then running an automated script that searches for open printer ports and sends out print jobs to the vulnerable devices. Speaking to Bleeping Computer, Stackoverflowin said the script targets printers that have IPP (Internet Printing Protocol) ports, LPD (Line Printer Daemon) ports, and port 9100 left open to external connections. The script also includes an exploit that uses a remote code execution vulnerability to target Dell Xeon printers. "This allowed me to inject PostScript and invoke rouge jobs," he told the publication.
Stackoverflowin stressed that there was no botnet and he just wanted to help people secure their devices from potential future attacks. "People have done this in the past and sent racist flyers [an incident from March last year] etc.. I'm not about that, I'm about helping people to fix their problem, but having a bit of fun at the same time ; ) Everyone's been cool about it and thanked me to be honest."
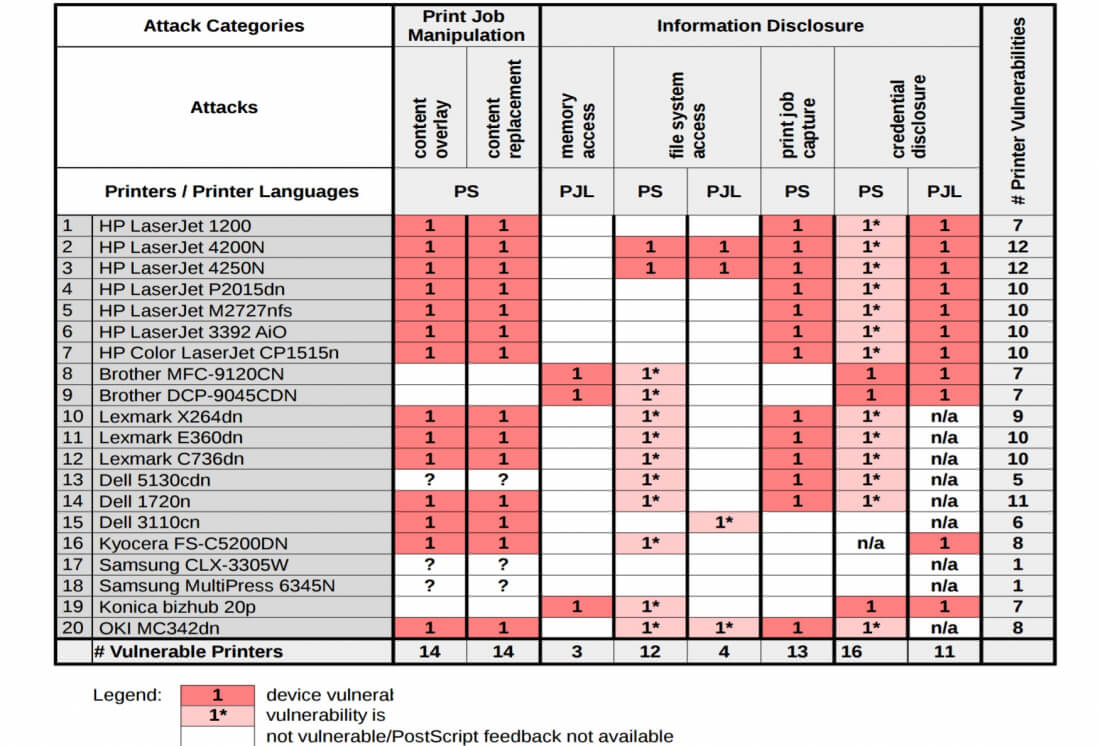
The attack followed a report by Jens Muller, Vladislav Mladenov and Juraj Somorovsky from the Ruhr University in Germany. It noted a number of vulnerabilities in printers from different manufacturers, including HP, Brother, Lexmark, Dell, Samsung, Konica, OKI, and Kyocera.
https://www.techspot.com/news/68041-hacker-takes-over-150000-internet-connected-printers-sends.html