In brief: If you're using SMS for two-factor authentication into your online accounts, you may want to change that as soon as possible. According to Princeton researchers, five of the largest US carriers are doing little to protect you from SIM swapping attacks, which give attackers an easy way to reset your passwords and access your sensitive data or impersonate you online.

While it's always a good idea to use multi-factor authentication to secure your online accounts, it doesn't mean you're entirely safe from everyone who wants to steal sensitive personal data.
According to a study from Princeton University, five of the largest US prepaid carriers fail to protect you against something referred to by experts as a "SIM-swap" attack. We have covered this type of theft several times in the past.
The way it works is an attacker persuades a carrier to reassign the victim's phone number to a new SIM card without going through all the standard security questions to verify their identity. This effectively allows the scammer to hijack someone's account and use two-factor authentication to reset passwords to important online accounts like email and bank accounts.
The researchers signed up for 50 prepaid accounts on Verizon, AT&T, T-Mobile, US Mobile, and Tracfone, and spent most of 2019 looking for ways they could trick call center operators into attaching their phone numbers to a new SIMs. What they found was that they only needed to respond successfully to one security challenge to get it done, even after multiple failed attempts, which they report didn't raise any red flags.
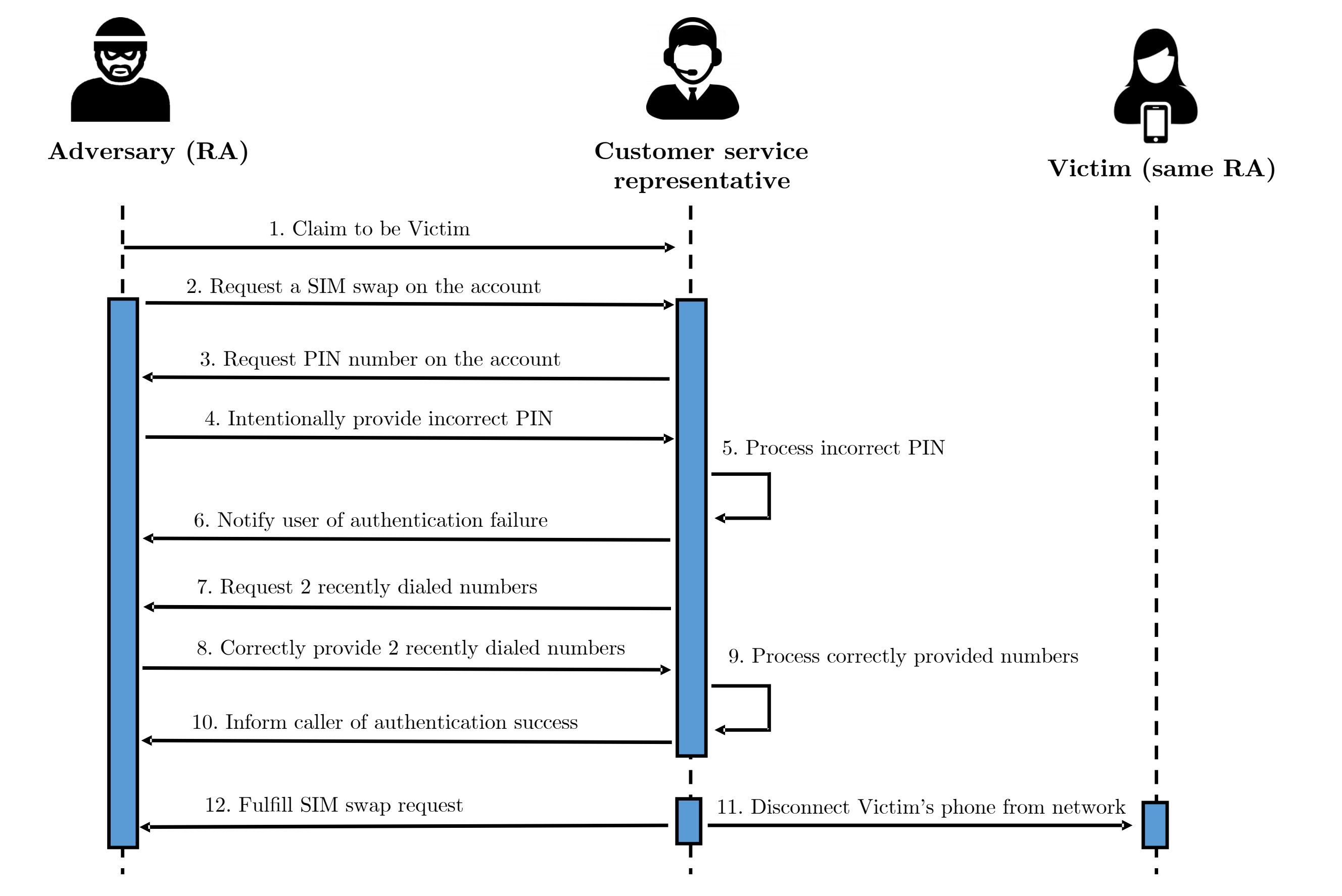
After intentionally providing wrong PINs, they were asked to verify other details like zip codes or other facts about the real account holder. The researchers told call center employees they couldn't recall that information, at which point, the standard procedure appeared to be to ask about the most recent two calls made from their number.
That is the weakness that makes the process exploitable. Attackers can easily trick someone into calling specific numbers using websites promising one thing or another. The researchers also found that 17 out of 140 online services using SMS for two-factor authentication don't employ any other method of verifying your identity, making it even easier for scammers to commit identity theft or steal victims' personal information.
The experts at Princeton notified the carriers, and T-Mobile told them earlier this month that it's no longer using call logs as an authentication method. Others, like Verizon and US Mobile, said they had received less than 1 percent of their SIM swapping requests over the phone, and that they are continually updating their cybersecurity practices.
The obvious conclusion is to stay away from using SMS as a form of two-factor authentication, and instead use an authenticator app. For those of you who own an Android phone, Google allows you to use your phone as a physical two-factor authentication key, which is about the safest method there is.
https://www.techspot.com/news/83528-princeton-study-shows-us-carriers-do-little-protect.html