Jesse
Posts: 358 +42

Technologically inclined individuals often stand out within their familial or social circles as a resource for the many complications that arise in our ever-expanding interconnected world. Generally speaking, we, the aforementioned ‘techies,’ advise that users should always follow certain best practices on the internet, such as verifying the identity of a website before handing over sensitive information, and always watching for an indication that a site is secure when doing so.
If your expectations of privacy on the web were not already fairly low, they were likely shattered in the past few weeks with the revelation of the PRISM program. But, the ramifications of this surveillance seem to pervade through forms of communication that many may have otherwise thought to be safe.
In addition to collecting standard unencrypted communication, PRISM is also gathering and storing mass quantities of SSL (secure sockets layer) encrypted data for later cryptanalysis. Netcraft reports that this large volume of data is logged so that if an SSL private key later becomes available through a variety of means, the entire batch of data collected from a particular site could be decrypted.
Private keys can be obtained through a number of means: a court order, social engineering, an attack against the website, or through cryptanalysis. Once exposed, a single key can decrypt the entire site’s worth of data.
This single point of failure was recognized long ago, and a solution was invented in 1992 called perfect forward security, or PFS. PFS requires connections to an SSL site to use a per-session key, which means that even if a long-term private key is compromised, a snooper (or government) would still have to attack each collected session independently.
Problem solved, right? Not quite. PFS hasn't been fully embraced, and is not used on a majority of SSL secured sites. It's similar to how inadequate and incongruous technologies are used for password storage that are getting internet companies into trouble lately. Many of them are not nearly as secure as they once were, and developers either don't know or don't care enough to use more robust alternatives.
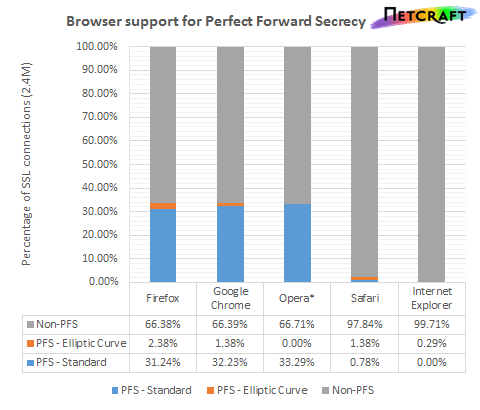
Netcraft points out that the web server Nginx, which uses PFS most often, was developed in Russia, a country commonly targeted by U.S. spies. Furthermore, none of the companies enrolled in the PRISM program use PFS.
While SSL may protect browsers from average eavesdroppers, these ‘secure’ communications are not at all infallible.