It should come as little surprise to learn that despite the spread of password managers, two-factor authentication, and the ever-increasing number of hacking incidents/data leaks, most people still use terrible passwords. A recent study by Virginia Tech University and Dashlane analyzed 61 million leaked credentials, which showed that bad habits remain prevalent when it comes to creating passwords.
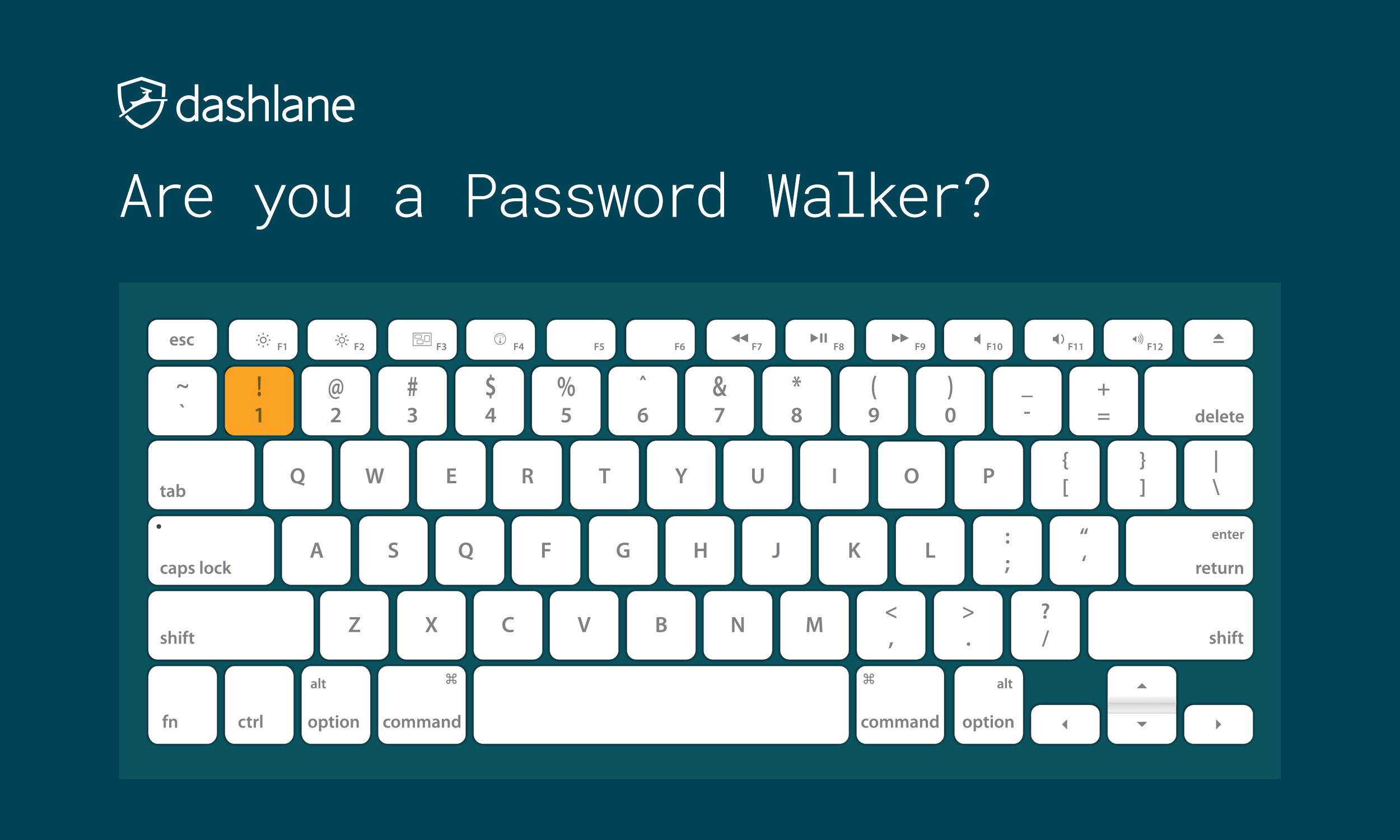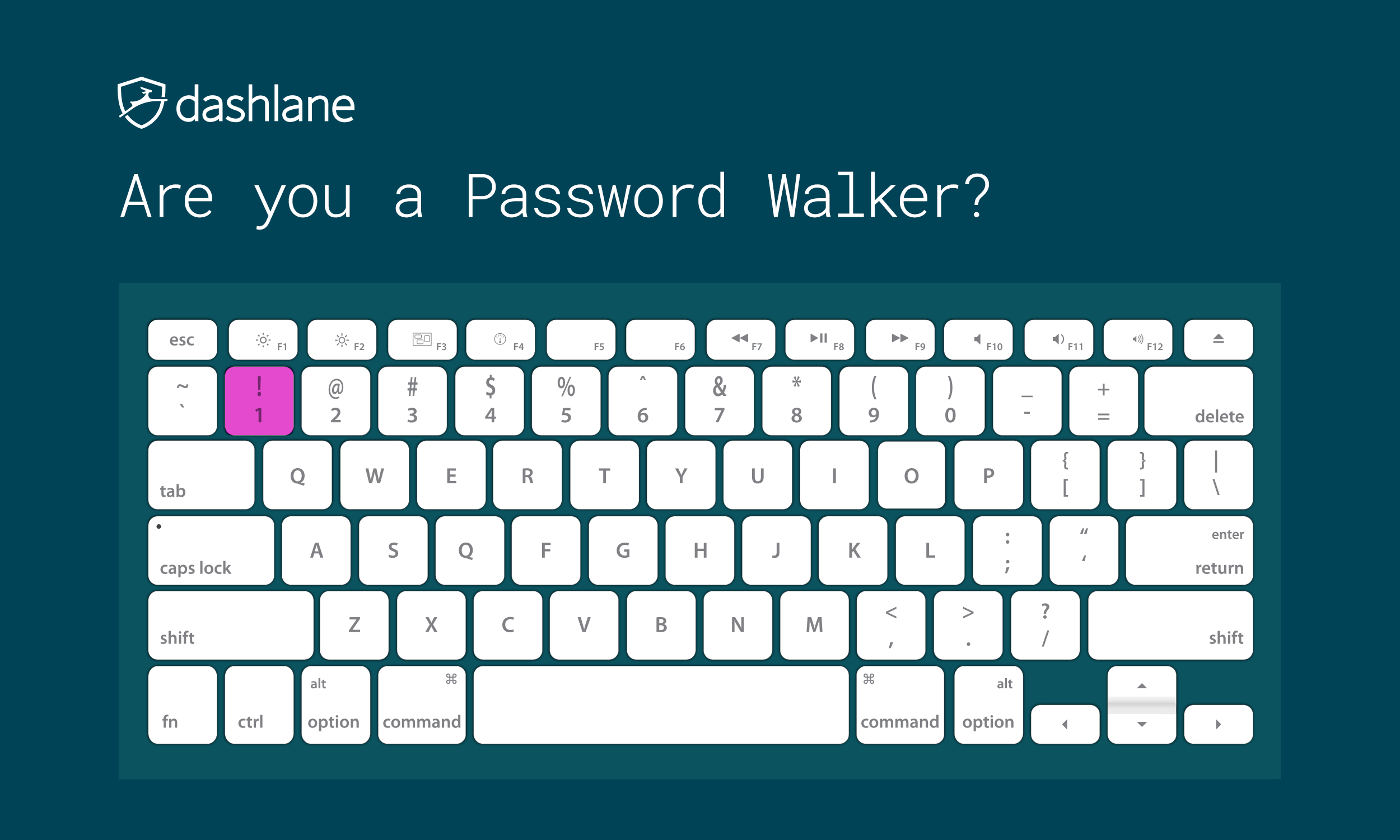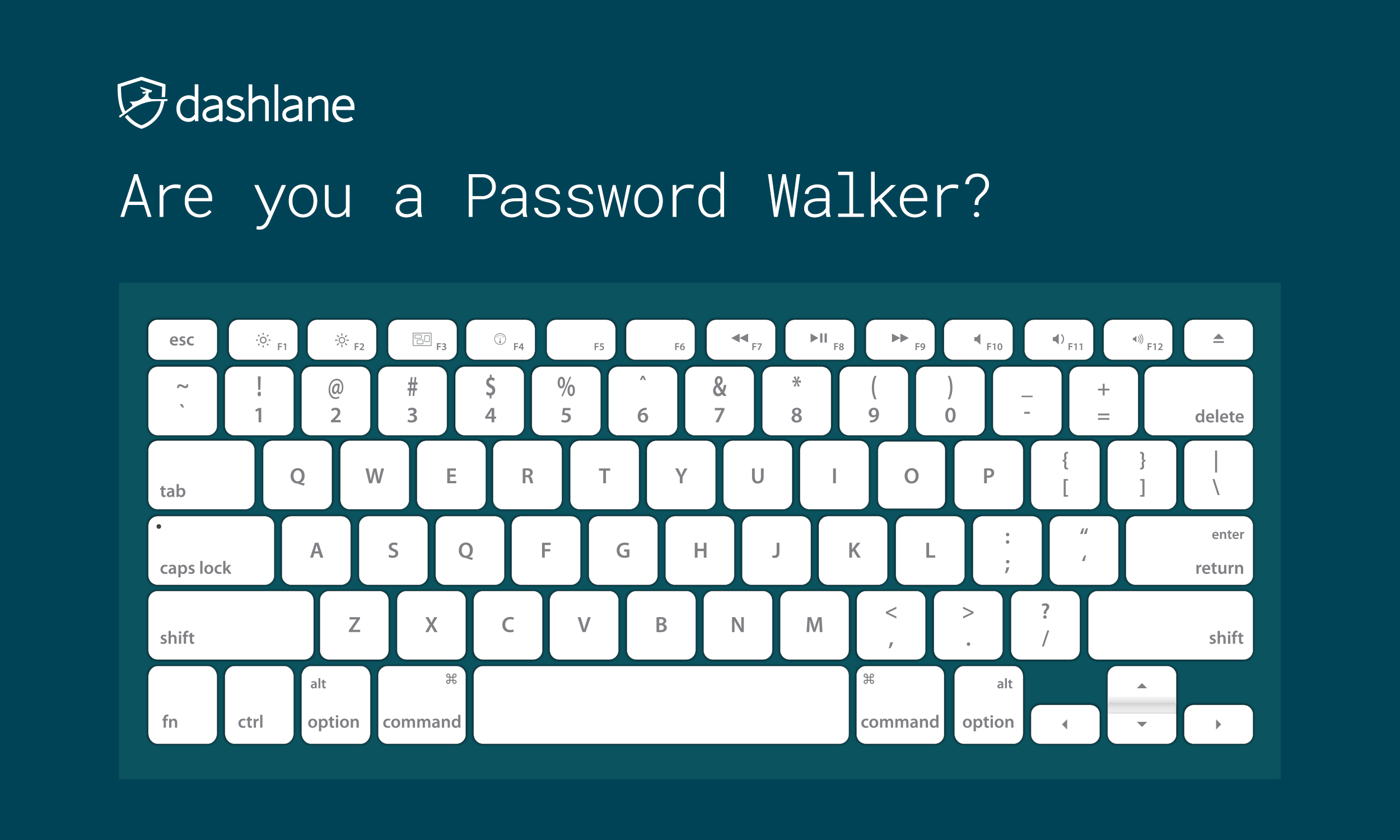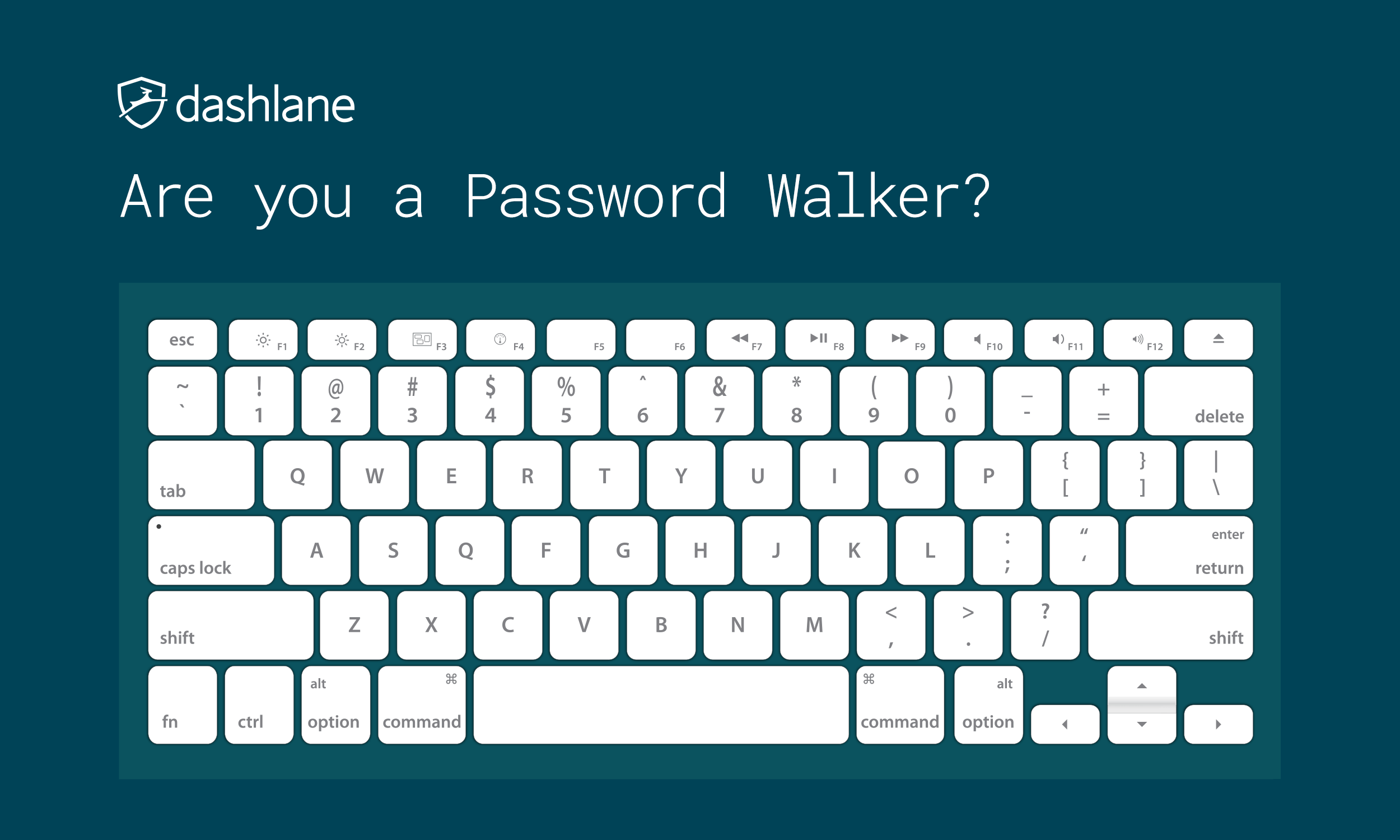
While the inexplicably popular 123456 and qwerty remain two of the most common picks, researchers found variations of these that use what is called “password walking.” The method involves picking numbers and letters adjacent to each other on a keyboard, leading to equally insecure passwords such as 1q2w3e4r and 1qaz2wsx.
It was also discovered that many people are quite passionate when it comes to choosing their passwords, with iloveyou, f**kyou, f**koff, and a**hole all popular choices. Pop culture picks included superman, pokemon, and slipknot, while soccer teams such as liverpool and barcelona also made the list.
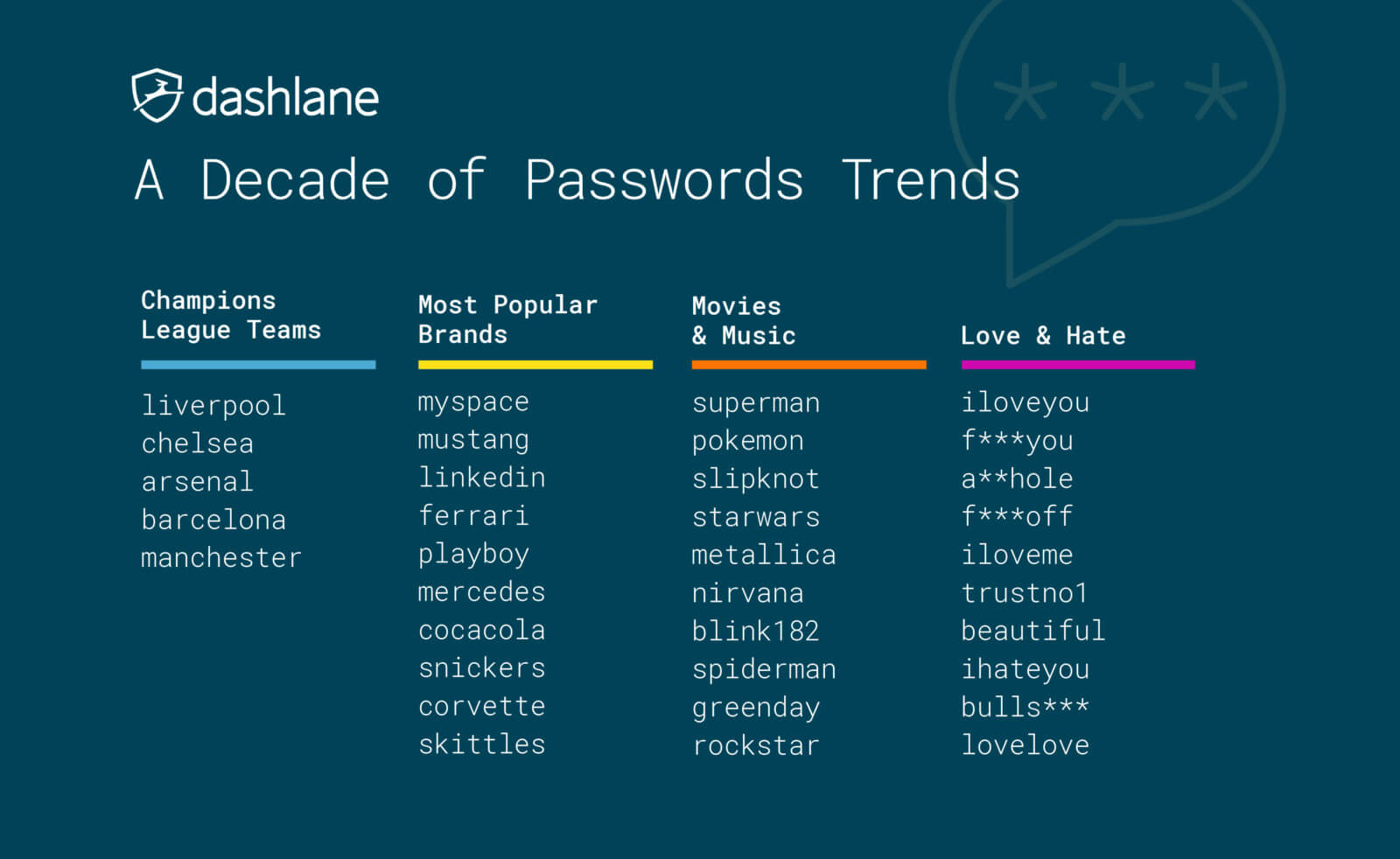
Brand names were very popular, too. Surprisingly, the most common of these is MySpace, with LinkedIn the third most common. It could be that many members of these services, which have experienced massive data leaks in the past, simply used the sites’ names as their passwords. Dashlane/Virginia tech analyzed leaks from the last eight years, which could explain their popularity in the dataset.
As always, the study shows why it’s best to follow password security best practices. Using 2FA, where available, is always advisable, despite it occasionally being a pain. And password managers like Dashlane can be a godsend, just don't use 123456 as master password.
https://www.techspot.com/news/74785-study-shows-most-people-bad-picking-passwords.html

