In context: The e-file system is the IRS' officially approved format for submitting tax documentation through the internet, usually with no need to provide any paper document. Netizens can use software programs or websites to submit their tax returns, even though using external services can lead to additional security risks.

Tax Day for US citizens is approaching fast, and cyber-criminals are exploiting the April 18 deadline to increase their malicious campaigns against users and legit tax-filing services. The eFile.com online platform recently got caught in this tax-related cybercrime resurgence, becoming a (likely) unaware spreader of malicious JavaScript files and malware payloads.
As reported by Bleeping Computer and confirmed by different security researchers, almost every page of the eFile website was serving a malicious JS script named "popper.js" at least until April 1st. The base64-encoded script was designed to load additional JS code from the infoamanewonliag dot online domain, which in turn would prompt users to download the actual malware payload named "update.exe" (for Chrome browsers) or "installer.exe" (Firefox).
Researchers confirmed that the executable binaries contained a Windows backdoor written in PHP, designed to establish a connection with a Tokyo-based IP address (47.245.6.91) hosted by Alibaba. The same IP was also hosting the infoamanewonliag domain pinged by the popper.js malicious script.
Once executed, the backdoor-carrying binary would run in the background, patiently waiting for orders coming from remote servers. The PHP script would connect to a command&control center every 10 seconds, and it could execute dangerous tasks like running a local command to send the output to the server, or downloading additional files on the compromised PC.
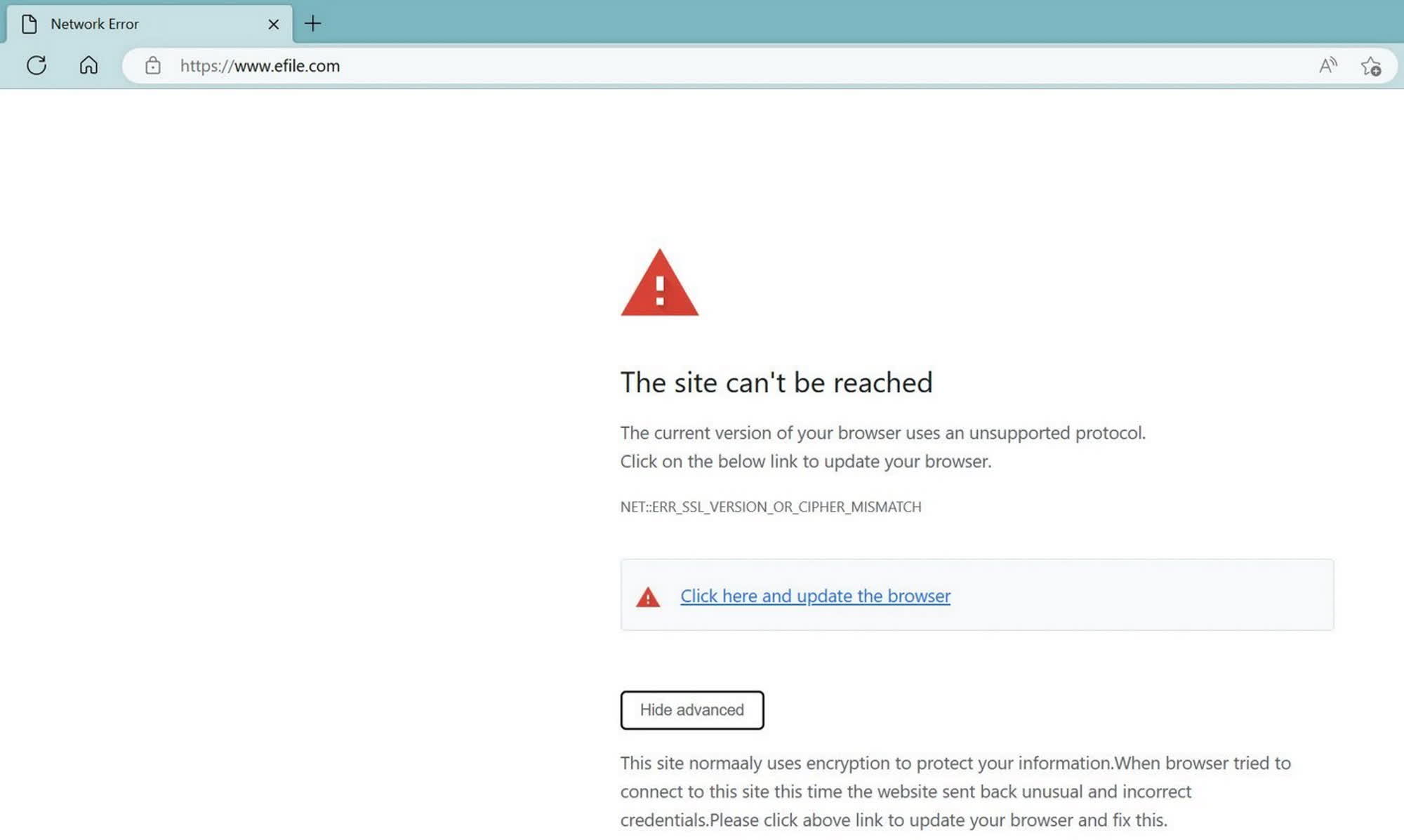
The backdoor-serving infection of eFile.com was seemingly already active in March, when a Reddit thread highlighted a possibly fake SSL error returned by the HTTPS-enabled website. The fake error was served by a malicious file named "update.js," which was designed to prompt users to download the aforementioned backdoored binary files update.exe and installer.exe.
While providing just the basic features for this kind of malicious software, the eFile backdoor was dangerous enough to give cyber-criminals full access to an infected Windows PC and further leverage to attack other systems in a corporate network. The eFile.com company still has to provide any explanation about the incident, while the cyber-gang behind the LockBit ransomware was claiming that they successfully attacked the website in January 2022 already.