wiyosaya
Posts: 9,763 +9,647
I've got *.techspot.com white-listed for cookies, yet starting today, I'm getting the following message along with failed postings and other issues:
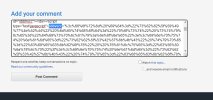
(Note when I tried to reply to a post, this appeared in the composition box. You'll have to decipher this yourselves, but it is the gist of the error I'm getting.)
<!DOCTYPE html> <html lang="en"> <head> <meta charset="utf-8"> <meta name="viewport" content="width=device-width, initial-scale=1, shrink-to-fit=no"> <title>Site verification</title> <script type="text/javascript"> function redirect(commitType){let cookieenabled=false;if(navigator.cookieEnabled){if(navigator.cookieEnabled==true){let exdate=new Date();exdate.setDate(exdate.getDate()+1);document.cookie="DGCC="+escape(genPid())+";path=/; SameSite=Lax; expires="+exdate.toGMTString();cookieenabled=(document.cookie.indexOf("DGCC")!=-1)? true : false;}}if(cookieenabled){if(commitType=="reload")window.location.reload(true);else{let oFrm=document.createElement("form");let oEnvlp=document.getElementById("frmPlsHldr");oFrm.method="post";oEnvlp.appendChild(oFrm);oFrm.submit();}}else{document.getElementById('JSCookieMSG').style.display='block';document.getElementById('JSCookieMSGHeader').style.display='block';}}</script> </head> <body> <div style="display:none" id="sbbhscc"></div><script type="text/javascript">sbbvscc='%3c%73%65%6c%65%63%74%20%69%64%3d%22%73%62%62%5f%64%78%6f%68%4c%50%22%20%73%74%79%6c%65%3d%22%64%69%73%70%6c%61%79%3a%6e%6f%6e%65%22%3e%3c%6f%70%74%69%6f%6e%20%20%76%61%6c%75%65%3d%27%56%77%7a%62%53%63%27%3e%74%64%47%59%3c%2f%6f%70%74%69%6f%6e%3e%3c%6f%70%74%69%6f%6e%20%53%45%4c%45%43%54%45%44%20%76%61%6c%75%65%3d%27%77%71%70%66%27%3e%75%61%77%79%3c%2f%6f%70%74%69%6f%6e%3e%3c%6f%70%74%69%6f%6e%20%20%76%61%6c%75%65%3d%27%42%4e%4c%5a%6b%27%3e%53%47%6e%79%7a%3c%2f%6f%70%74%69%6f%6e%3e%3c%6f%70%74%69%6f%6e%20%20%76%61%6c%75%65%3d%27%5a%74%4b%54%27%3e%57%56%5a%6d%3c%2f%6f%70%74%69%6f%6e%3e%3c%2f%73%65%6c%65%63%74%3e';sbbgscc='%66%75%6e%63%74%69%6f%6e%20%73%62%62%5f%79%7a%45%55%4a%28%29%20%7b%20%75%76%6f%67%71%20%3d%20%74%79%70%65%6f%66%20%31%37%37%32%3b%20%72%65%74%75%72%6e%20%53%74%72%69%6e%67%2e%66%72%6f%6d%43%68%61%72%43%6f%64%65%28%75%76%6f%67%71%2e%63%68%61%72%43%6f%64%65%41%74%28%34%29%5e%35%30%29%3b%20%7d%66%75%6e%63%74%69%6f%6e%20%73%62%62%5f%7a%78%45%74%61%64%28%29%20%7b%20%52%42%79%4d%69%3d%28%34%33%29%2b%4d%61%74%68%2e%66%6c%6f%6f%72%28%28%28%28%28%28%28%28%28%28%28%28%28%38%36%29%20%2a%20%33%35%29%20%2d%20%39%37%29%20%2b%20%39%36%29%20%2d%20%31%35%29%20%2d%20%33%36%29%20%2b%20%34%31%29%20%2b%20%31%36%29%20%2a%20%38%34%29%20%2f%20%37%37%29%20%2b%20%39%38%29%20%2d%20%35%30%29%20%2f%20%39%33%29%3b%20%72%65%74%75%72%6e%20%53%74%72%69%6e%67%2e%66%72%6f%6d%43%68%61%72%43%6f%64%65%28%52%42%79%4d%69%29%3b%20%7d%66%75%6e%63%74%69%6f%6e%20%73%62%62%5f%62%73%6d%64%77%4d%28%29%20%7b%20%73%62%62%4f%62%6a%20%3d%20%64%6f%63%75%6d%65%6e%74%2e%67%65%74%45%6c%65%6d%65%6e%74%42%79%49%64%28%22%73%62%62%5f%64%78%6f%68%4c%50%22%29%3b%20%73%62%62%4f%62%6a%2e%6f%70%74%69%6f%6e%73%5b%33%5d%2e%73%65%6c%65%63%74%65%64%20%3d%20%74%72%75%65%3b%20%72%65%74%75%72%6e%20%73%62%62%4f%62%6a%2e%6f%70%74%69%6f%6e%73%5b%73%62%62%4f%62%6a%2e%73%65%6c%65%63%74%65%64%49%6e%64%65%78%5d%2e%76%61%6c%75%65%2e%73%75%62%73%74%72%28%30%2c%31%29%3b%20%7d;function genPid() {return %73%62%62%5f%79%7a%45%55%4a%28%29%2b%73%62%62%5f%7a%78%45%74%61%64%28%29%2b%73%62%62%5f%62%73%6d%64%77%4d%28%29;}';</script><div id="sbbfrcc" style="position:absolute;top:-10px;left:30px;font-size:1px"></div> <div class="layout"> <noscript> <div style="position: fixed;top: 0px;left: 0px;z-index: 2000;height: 100%;width: 100%;background-color: #FFFFFF"> </div> <div class="layout__main" style="z-index: 3000;position: fixed;margin: auto;"> <h1>Please Enable JavaScript</h1> <p> <strong>www.techspot.com</strong> is using a security service for protection against online attacks.<br /> The service requires full JavaScript support in order to view this website. </p> <p>Please enable JavaScript on your browser and try again. </p> </div> </noscript> <div class="layout__main" id='main'> <p> <h1 id='JSCookieMSGHeader' style="display:none">Please Enable Cookies</h1> </p> <p> <strong>www.techspot.com</strong> is using a security service for protection against online attacks.<br /> This process is automatic. You will be redirected once the validation process is complete. </p> <p id='JSCookieMSG' style="display:none"> Please enable cookies on your browser and try again. </p> </div> <div id='frmPlsHldr'></div> </div> <script type="text/javascript"> try{y=unescape(sbbvscc.replace(/^<\!\-\-\s*|\s*\-\->$/g, ''));document.getElementById('sbbhscc').innerHTML=y;x=unescape(sbbgscc.replace(/^<\!\-\-\s*|\s*\-\->$/g, ''));}catch(e){x='function genPid(){return "jser";}';}document.write('<'+'script type="text/javascri'+'pt">'+x+' redirect("post");</'+'script>');</script> </body> </html>
(Note when I tried to reply to a post, this appeared in the composition box. You'll have to decipher this yourselves, but it is the gist of the error I'm getting.)
<!DOCTYPE html> <html lang="en"> <head> <meta charset="utf-8"> <meta name="viewport" content="width=device-width, initial-scale=1, shrink-to-fit=no"> <title>Site verification</title> <script type="text/javascript"> function redirect(commitType){let cookieenabled=false;if(navigator.cookieEnabled){if(navigator.cookieEnabled==true){let exdate=new Date();exdate.setDate(exdate.getDate()+1);document.cookie="DGCC="+escape(genPid())+";path=/; SameSite=Lax; expires="+exdate.toGMTString();cookieenabled=(document.cookie.indexOf("DGCC")!=-1)? true : false;}}if(cookieenabled){if(commitType=="reload")window.location.reload(true);else{let oFrm=document.createElement("form");let oEnvlp=document.getElementById("frmPlsHldr");oFrm.method="post";oEnvlp.appendChild(oFrm);oFrm.submit();}}else{document.getElementById('JSCookieMSG').style.display='block';document.getElementById('JSCookieMSGHeader').style.display='block';}}</script> </head> <body> <div style="display:none" id="sbbhscc"></div><script type="text/javascript">sbbvscc='%3c%73%65%6c%65%63%74%20%69%64%3d%22%73%62%62%5f%64%78%6f%68%4c%50%22%20%73%74%79%6c%65%3d%22%64%69%73%70%6c%61%79%3a%6e%6f%6e%65%22%3e%3c%6f%70%74%69%6f%6e%20%20%76%61%6c%75%65%3d%27%56%77%7a%62%53%63%27%3e%74%64%47%59%3c%2f%6f%70%74%69%6f%6e%3e%3c%6f%70%74%69%6f%6e%20%53%45%4c%45%43%54%45%44%20%76%61%6c%75%65%3d%27%77%71%70%66%27%3e%75%61%77%79%3c%2f%6f%70%74%69%6f%6e%3e%3c%6f%70%74%69%6f%6e%20%20%76%61%6c%75%65%3d%27%42%4e%4c%5a%6b%27%3e%53%47%6e%79%7a%3c%2f%6f%70%74%69%6f%6e%3e%3c%6f%70%74%69%6f%6e%20%20%76%61%6c%75%65%3d%27%5a%74%4b%54%27%3e%57%56%5a%6d%3c%2f%6f%70%74%69%6f%6e%3e%3c%2f%73%65%6c%65%63%74%3e';sbbgscc='%66%75%6e%63%74%69%6f%6e%20%73%62%62%5f%79%7a%45%55%4a%28%29%20%7b%20%75%76%6f%67%71%20%3d%20%74%79%70%65%6f%66%20%31%37%37%32%3b%20%72%65%74%75%72%6e%20%53%74%72%69%6e%67%2e%66%72%6f%6d%43%68%61%72%43%6f%64%65%28%75%76%6f%67%71%2e%63%68%61%72%43%6f%64%65%41%74%28%34%29%5e%35%30%29%3b%20%7d%66%75%6e%63%74%69%6f%6e%20%73%62%62%5f%7a%78%45%74%61%64%28%29%20%7b%20%52%42%79%4d%69%3d%28%34%33%29%2b%4d%61%74%68%2e%66%6c%6f%6f%72%28%28%28%28%28%28%28%28%28%28%28%28%28%38%36%29%20%2a%20%33%35%29%20%2d%20%39%37%29%20%2b%20%39%36%29%20%2d%20%31%35%29%20%2d%20%33%36%29%20%2b%20%34%31%29%20%2b%20%31%36%29%20%2a%20%38%34%29%20%2f%20%37%37%29%20%2b%20%39%38%29%20%2d%20%35%30%29%20%2f%20%39%33%29%3b%20%72%65%74%75%72%6e%20%53%74%72%69%6e%67%2e%66%72%6f%6d%43%68%61%72%43%6f%64%65%28%52%42%79%4d%69%29%3b%20%7d%66%75%6e%63%74%69%6f%6e%20%73%62%62%5f%62%73%6d%64%77%4d%28%29%20%7b%20%73%62%62%4f%62%6a%20%3d%20%64%6f%63%75%6d%65%6e%74%2e%67%65%74%45%6c%65%6d%65%6e%74%42%79%49%64%28%22%73%62%62%5f%64%78%6f%68%4c%50%22%29%3b%20%73%62%62%4f%62%6a%2e%6f%70%74%69%6f%6e%73%5b%33%5d%2e%73%65%6c%65%63%74%65%64%20%3d%20%74%72%75%65%3b%20%72%65%74%75%72%6e%20%73%62%62%4f%62%6a%2e%6f%70%74%69%6f%6e%73%5b%73%62%62%4f%62%6a%2e%73%65%6c%65%63%74%65%64%49%6e%64%65%78%5d%2e%76%61%6c%75%65%2e%73%75%62%73%74%72%28%30%2c%31%29%3b%20%7d;function genPid() {return %73%62%62%5f%79%7a%45%55%4a%28%29%2b%73%62%62%5f%7a%78%45%74%61%64%28%29%2b%73%62%62%5f%62%73%6d%64%77%4d%28%29;}';</script><div id="sbbfrcc" style="position:absolute;top:-10px;left:30px;font-size:1px"></div> <div class="layout"> <noscript> <div style="position: fixed;top: 0px;left: 0px;z-index: 2000;height: 100%;width: 100%;background-color: #FFFFFF"> </div> <div class="layout__main" style="z-index: 3000;position: fixed;margin: auto;"> <h1>Please Enable JavaScript</h1> <p> <strong>www.techspot.com</strong> is using a security service for protection against online attacks.<br /> The service requires full JavaScript support in order to view this website. </p> <p>Please enable JavaScript on your browser and try again. </p> </div> </noscript> <div class="layout__main" id='main'> <p> <h1 id='JSCookieMSGHeader' style="display:none">Please Enable Cookies</h1> </p> <p> <strong>www.techspot.com</strong> is using a security service for protection against online attacks.<br /> This process is automatic. You will be redirected once the validation process is complete. </p> <p id='JSCookieMSG' style="display:none"> Please enable cookies on your browser and try again. </p> </div> <div id='frmPlsHldr'></div> </div> <script type="text/javascript"> try{y=unescape(sbbvscc.replace(/^<\!\-\-\s*|\s*\-\->$/g, ''));document.getElementById('sbbhscc').innerHTML=y;x=unescape(sbbgscc.replace(/^<\!\-\-\s*|\s*\-\->$/g, ''));}catch(e){x='function genPid(){return "jser";}';}document.write('<'+'script type="text/javascri'+'pt">'+x+' redirect("post");</'+'script>');</script> </body> </html>