Bottom line: Security researchers have devised a new way to steal cryptographic keys in Secure Shell (SSH) computer-to-server communication. Compromised SSH connections could allow bad actors to monitor or exfiltrate data exchanged between enterprise servers and remote clients. The study builds on research over the last 25 years.
The exploit leverages minor computational errors naturally occurring during the SSH handshake. Fortunately, it only works for RSA encryption. Unfortunately, RSA algorithms account for about one-third of the sites tested. Out of roughly 3.5 billion signatures examined from public websites scanned over the last seven years, about one billion used RSA. In that subgroup, about one in a million implementations exposed their SSH keys.
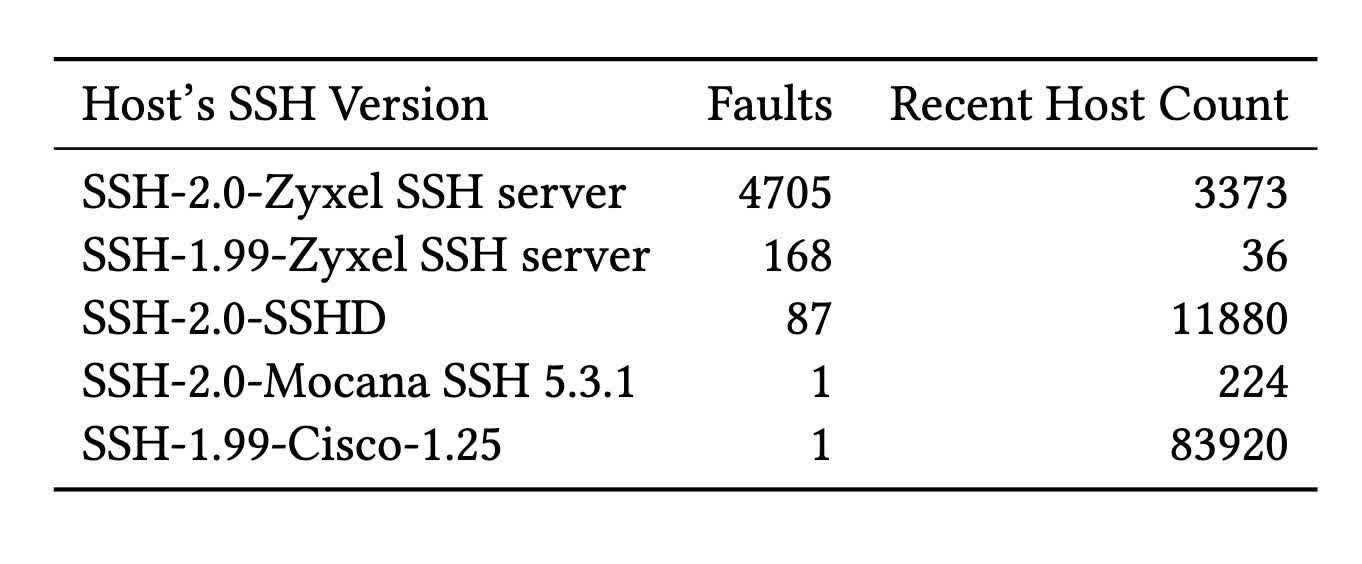
"In our data, about one in a million SSH signatures exposed the private key of the SSH host," co-author Keegan Ryan told Ars Technica. "While this is rare, the massive amount of traffic on the Internet implies that these RSA faults in SSH happen regularly."
To make matters worse, hackers could use the same or a similar technique to compromise IPsec connections. In their recently published paper "Passive SSH Key Compromise via Lattices," the researchers point out that it could spell doom to companies or individuals using VPNs to secure their connections and hide their internet traffic.
"In this paper, we show that passive RSA key recovery from a single PKCS#1 v1.5-padded faulty signature is possible in the SSH and IPsec protocols using a lattice attack described by Coron et al," the study's introduction reads.
The legacy exploit intentionally caused an error in the handshake by disrupting the process. Alternatively, attackers could passively wait for one to occur. After capturing the faulty signature, it is compared to a valid one using a "greatest common denominator" operation to retrieve one of the prime numbers securing the key. However, this new attack uses an off-shoot of lattice-based cryptography.
Once attackers have the key, they can set up a man-in-the-middle attack. The hacker-controlled server uses the ill-gotten key to impersonate the compromised server, intercepting and responding to incoming SSH communication. From there, credentials and other information are easily stolen. The same can happen with IPsec traffic if attackers gain a faulty key.
The group primarily found the weakness in devices from four manufacturers – Cisco, Zyxel, Hillstone Networks, and Mocana. The researchers informed the OEMs about the vulnerability before publishing. Only Cisco and Zyxel responded immediately – Hillstone replied after publication.
Recent mitigations in Transport Layer Security have strengthened its defenses against such attacks. Ryan says that other secure protocols must implement similar measures, especially SSH and IPsec since they are so widely used. Even still, individual risks to these types of hacks are relatively low.
You can read or download all the technical details in the paper from the Cryptology ePrint Archive website.
Image credit: Keegan Ryan et al.
